HKCERT 2025 - MISC Writeup
HKCERT - 2025 - Misc
Little Wish
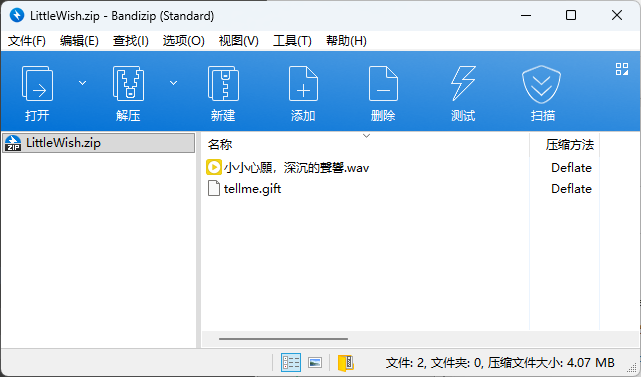
下载附件,得到两个文件
tellme.gift与小小心願,深沉的聲響.wav
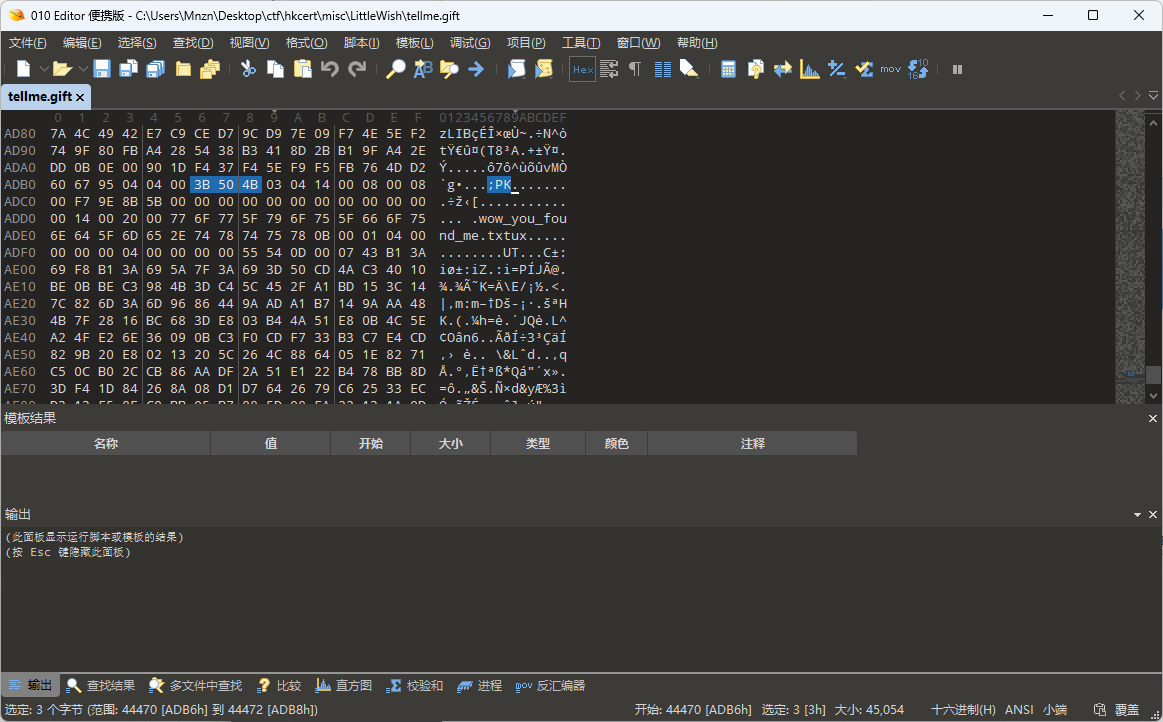
Step1
tellme.gift的文件尾部有一个压缩包 可用 Binwalk 压缩包内是wow_you_found_me.txt
Ⅰ. Look at that, what is "9a" ...? And what is the difference between "9a" and "7a"?
Ⅱ. Seek out the "P" above all, since the key clue lies there.
Ⅲ. But what is "P"? It can't be a pillow, right? Because if it were, I'd want to go to bed right now! (-:
̷͒͘Ⅳ̧͓̄.̹̀͒
̛͍̑?̻̀̆
̼̐͘Ȃ̴͍
̢͓̄n̵̻͗
̢͎̐y̴̻͒
̧͎̄t͈̐͘
̹̕h̷̨
͓̕į̻
̢͇͒n̵͓̐
͓̀̍g̶͓̅
̵̹̎é͓̿
́l̢
͇́̆s̡̻̐
͉͒͘e̢̼̿
͎̐͘?̧͉̄ 猜测提示I的 between "9a" and "8a" 为修复正确GIF文件头 "GIF89a"
修复出正确的gif文件,读取出帧间隔,除以10后 ASCII 解码即可得到 MENGMENG_XIANG
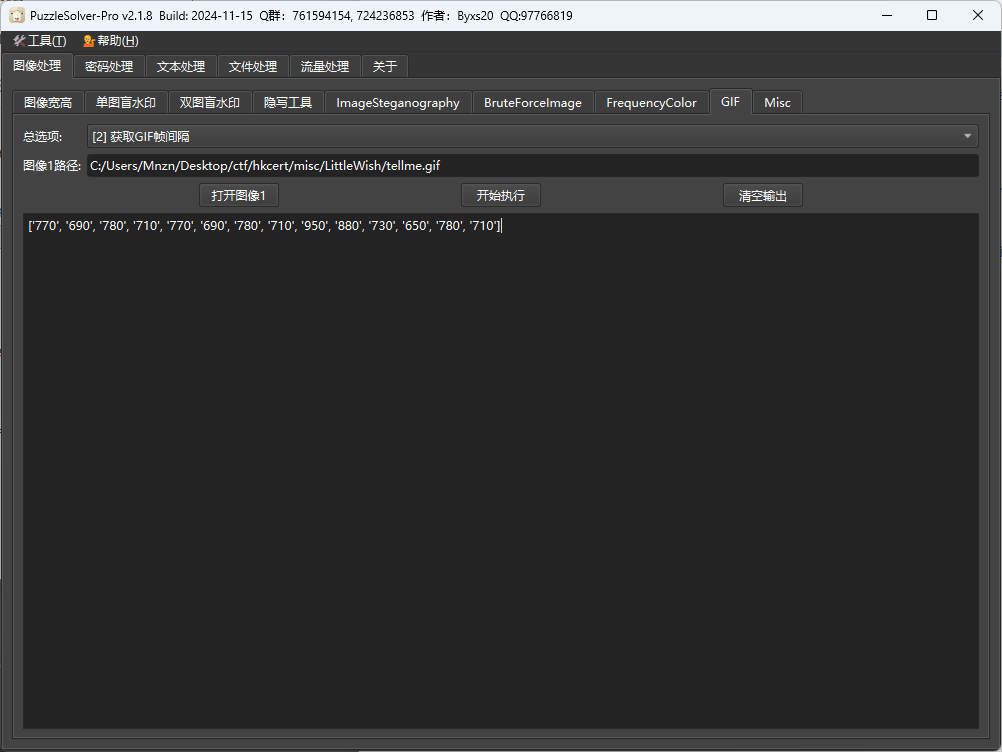
Step2
wav文件名 深沉的聲響 猜测是DeepSound隐写,尝试解密
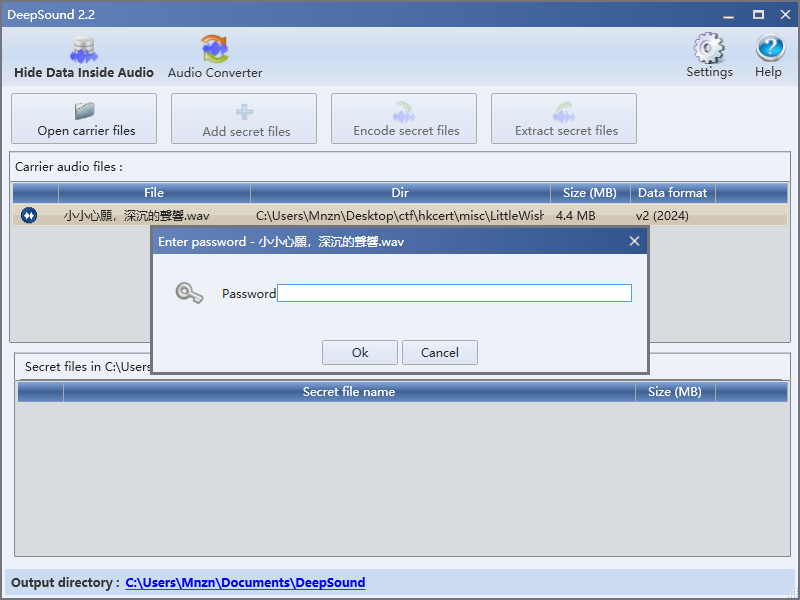
使用Step1得到的MENGMENG_XIANG作为密钥,得到加密的 flag.zip
Step3
提示 II、III还没用到,询问AI,猜测 P 指的是 Palette 调色板
即 GIF 中的 Global Color Table 数据
F2 D1 AF F5 CA 98 FA C8 88 F9 B7 7B F2 B1 6F EF
B6 91 F1 B6 82 E9 B2 86 D8 B2 97 F9 AD 68 F9 AC
52 FB A6 33 FA 99 16 F4 96 49 FB 94 0B EE 92 4E
EC 9B 6B D0 96 6D F4 8B 34 EB 8C 4F F3 91 35 F5
8E 2B EA 86 35 EB 7D 49 F2 87 17 F7 88 08 F4 74
32 EB 77 34 EC 73 2C F3 6E 2B D7 89 54 D8 81 38
E6 79 17 E8 76 08 DC 71 04 D3 6D 15 AC 89 6E CE
74 49 97 6E 57 EB 67 29 EA 69 29 E7 66 12 D7 6A
06 D3 6A 2B CD 6B 27 D5 68 09 CC 62 07 EA 5A 15
E4 59 14 DF 5F 23 DD 57 14 E3 54 0C DC 53 0B CA
5A 09 B1 5C 24 AE 58 17 AC 67 35 8A 55 30 8E 4B
14 7D 47 1A 73 3D 12 64 5A 53 6D 46 2C 4D 3E 33
54 2D 11 32 2C 29 46 2A 16 3D 28 1B 2F 15 05 19
12 0F 16 0B 02 09 06 04 00 01 01 00 01 01 01 01
00 01 00 01 01 01 01 01 00 01 00 00 00 01 01 01
00 01 01 00 00 01 00 01 00 01 01 01 00 01 00 00
00 01 00 01 01 01 01 01 00 01 00 00 00 00 00 01
00 01 01 00 00 01 01 00 00 01 01 01 00 01 00 00
00 01 01 00 00 01 00 01 00 01 01 01 00 00 01 00
00 01 00 01 01 01 01 01 00 00 01 01 00 00 01 00
00 00 01 01 00 00 01 01 00 00 01 01 00 01 01 01
00 01 00 01 01 01 01 01 00 01 00 01 00 00 00 00
00 01 01 01 00 01 00 01 00 01 01 00 01 01 00 00
00 01 01 00 01 01 00 00 00 01 01 01 00 00 01 01将前半段数据 与0x01按位与(lsb)得到一串新的00、01序列
再将完整数据 00 -> 0 01 -> 1
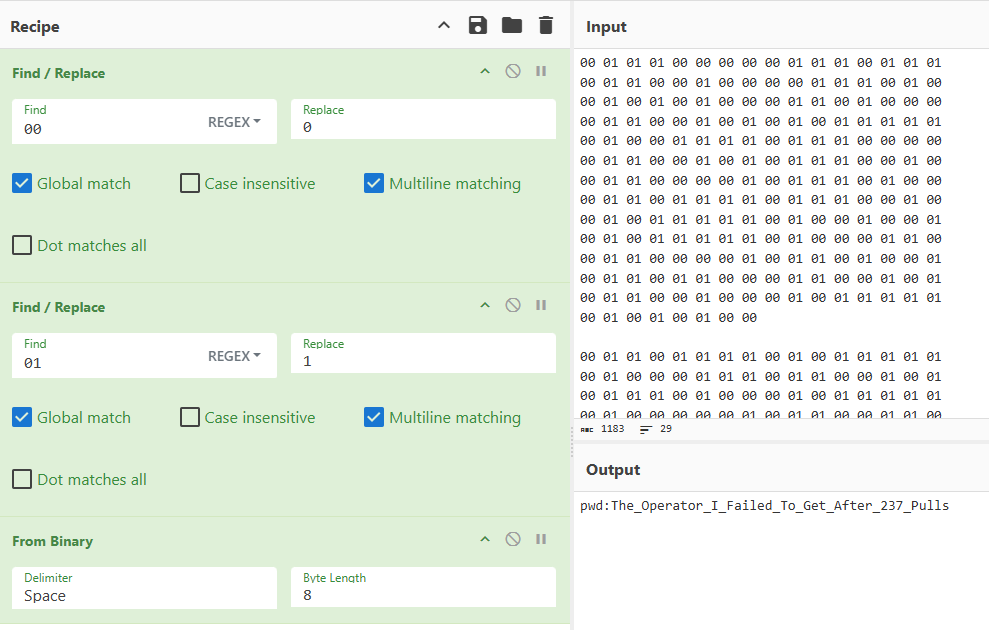
得到压缩包密码 The_Operator_I_Failed_To_Get_After_237_Pulls
解压得到flag flag{1Ch1B4n_SuK1_N4_W4t4sh1_N1N4RuN0~}
easyJail
Pickle 反序列化,AI梭了
exp
# pylint: disable = unnecessary-lambda-assignment, protected-access, redefined-builtin
import pickle
from io import BytesIO
from base64 import b64decode
_dispatch = pickle._Unpickler.dispatch
_noop = lambda *_: None
_noop_code = _noop.__code__
_DISABLED_OPCODES = [
pickle.NEWOBJ_EX[0],
pickle.INST[0],
pickle.REDUCE[0],
pickle.OBJ[0],
pickle.NEWOBJ[0],
]
for opcode in _DISABLED_OPCODES:
_dispatch.pop(opcode)
pickle._Unpickler.dispatch = _dispatch
for method_name in (
"load_newobj_ex",
"load_obj",
"load_reduce",
"load_newobj",
"load_inst",
):
handler = getattr(pickle._Unpickler, method_name)
handler.__code__ = _noop_code
__builtins__ = {
"input": input,
"ValueError": ValueError,
"bytes": bytes,
"isinstance": isinstance,
}
del _dispatch
del _noop
del _noop_code
del _DISABLED_OPCODES
del opcode
_BLACKLISTED_SUBSTRINGS = {
"var",
"input",
"builtin",
"set",
"get",
"import",
"open",
"subprocess",
"sys",
"eval",
"exec",
"os",
"compile",
}
def loads(data: bytes):
if not isinstance(data, bytes):
raise TypeError("expected bytes")
for token in _BLACKLISTED_SUBSTRINGS:
if token.encode() in data:
raise ValueError(f"{token} not allowed")
buffer = BytesIO(data)
return pickle._Unpickler(buffer).load()
opcode = b64decode(input("Enter your pickle: ").encode())
del b64decode
loads(opcode)busbus
Modbus协议 有点猜迷
https://goodlunatic.github.io/posts/01ebd40/
传输标识符2B+协议标识符2B+长度2B+从机ID 1B+功能码1B+数据字段xB
功能码
1:读线圈
2:读离散输入
3:读保持
4:读输入
5:写单个线圈
6:写单个保持
15:写多个线圈
16:写多个保持
题目说是backdoor,需要trigger
解题方法是通过 FC15 向线圈内写入 'open' 的 8-bit ASCII 序列 后触发后门
再通过 FC03 读寄存器得到flag,虽然不知道为什么是open,但是就是open,fuzz
Deleted
取证
Q1) What is the computer username? e.g: bob
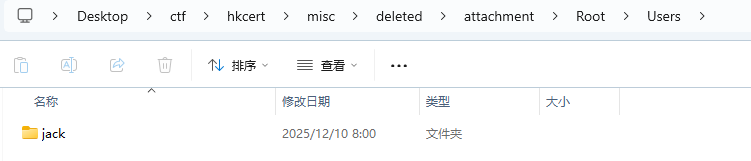
Root\Users\jack
jack
Q2) What is the device name? e.g: desktop-1d76lc4
Format: [a-z0-9-]+
在Root\Users\jack\AppData\Roaming\uTools\clipboard-data\1765137507668
有一个ebc82002a9d84b6978f70cd856581125文件,是png 显示了用户名
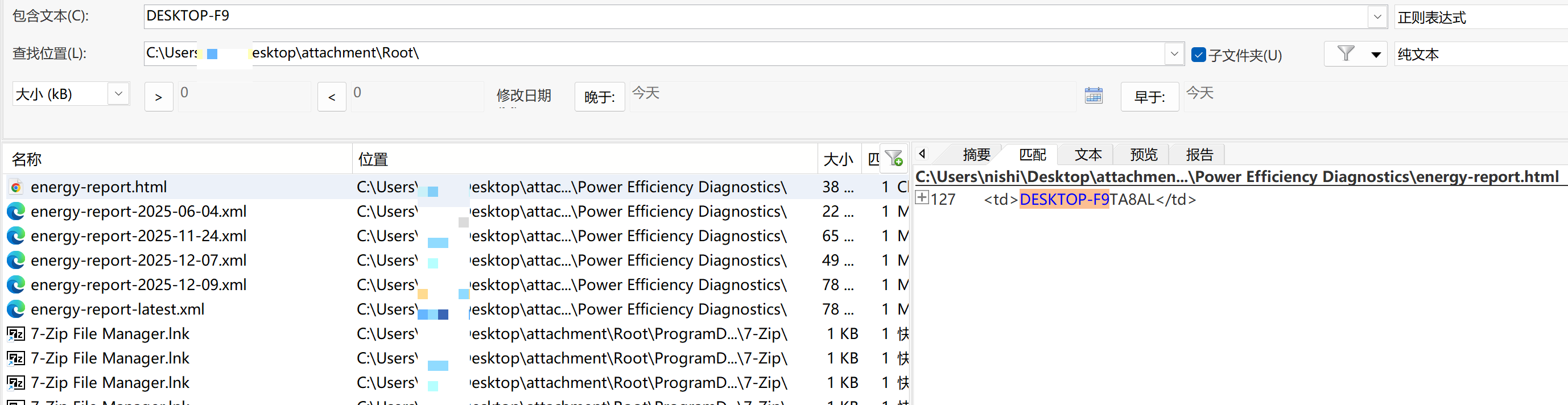
desktop-f9ta8al
Q3) What is the last time the device was shut down? Please provide your answer in UTC+8 timezone. e.g: e4d8b17ba7bdea5df12552034245edd7
Format: md5(YYYY/MM/DD HH:MM:SS).lowercase()
注册表 => Root\Windows\System32\config\SYSTEM
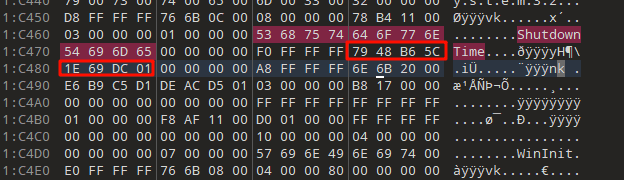
记录了以 小端序FILETIME 存储的 ShutdownTime
转换为 UTC+8 即可: 2025-12-09 23:13:23
e1a465a0bd5e8f9fe35651ee71689a5f
Q4) What is the code word for the rendezvous planned by the suspect? e.g: c2443fd7e6e158b9497c3fde067af076
Format: md5(req:res).lowercase()
Root\Users\jack\AppData\Roaming\CherryStudio\IndexedDB\file__0.indexeddb.leveldb\000003.log
这里有一个 CherryStudio 的 ai 对话记录
UTF-16LE编码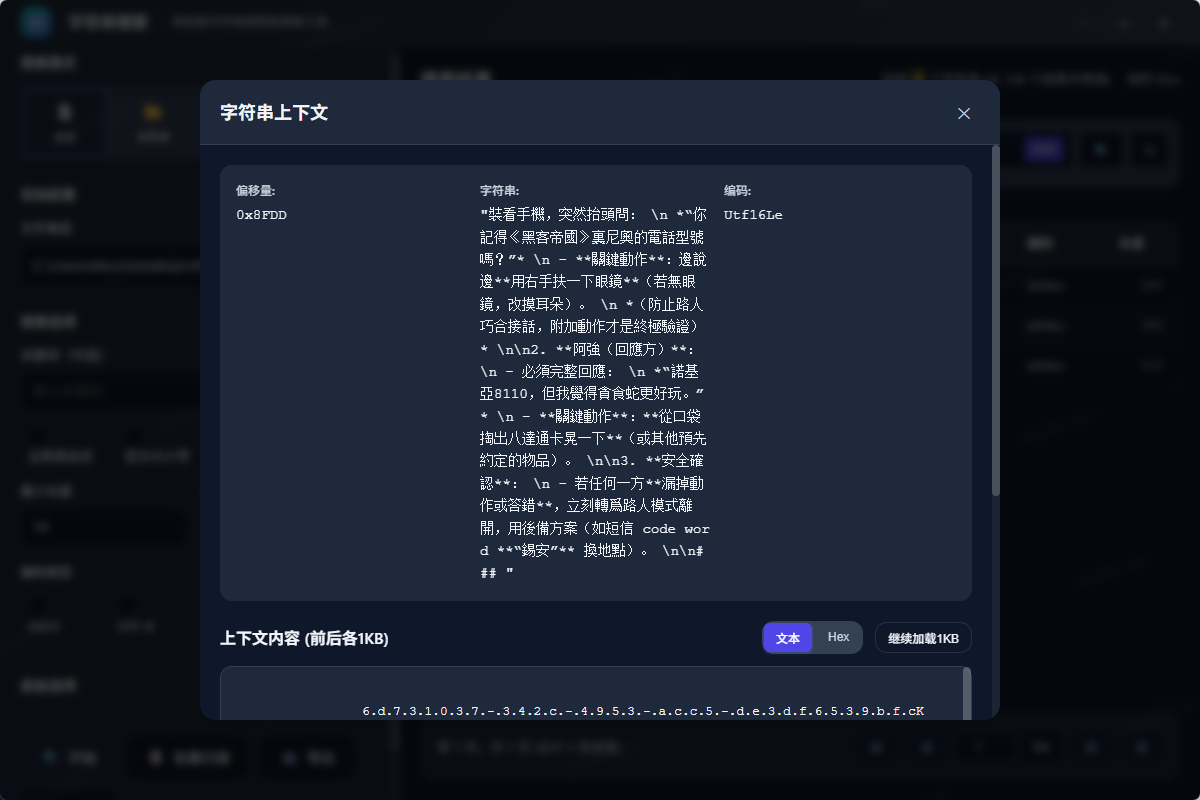
暗号:你記得《黑客帝國》裏尼奧的電話型號嗎?:諾基亞8110,但我覺得貪食蛇更好玩。
93f91a283267c82e8baa9ae10b38bc1b
Q5 What instant messaging software did the suspect once use? e.g: line
Root\Users\jack\AppData\Local\SquirrelTemp 有 Discord 的卸载记录
ShimCache 也能看到相关记录
Q6 社交软件密码
在与 AI 的对话中还能看到,嫌疑人让ai生成了一个密码算法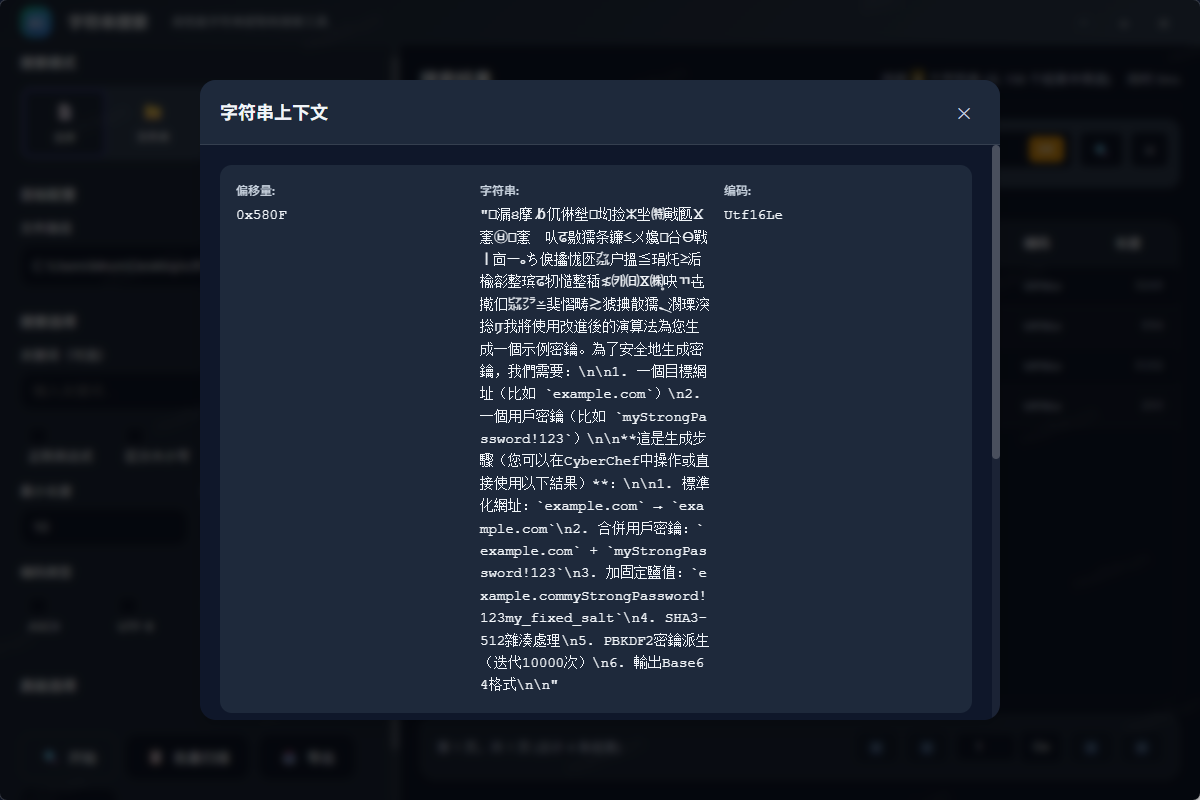
不过这里的 CyberChef Recipe 是假的,而CyberChef的算法流程是在url中保存的

可以直接从Edge的记录中字符串搜到真正的url得到recipe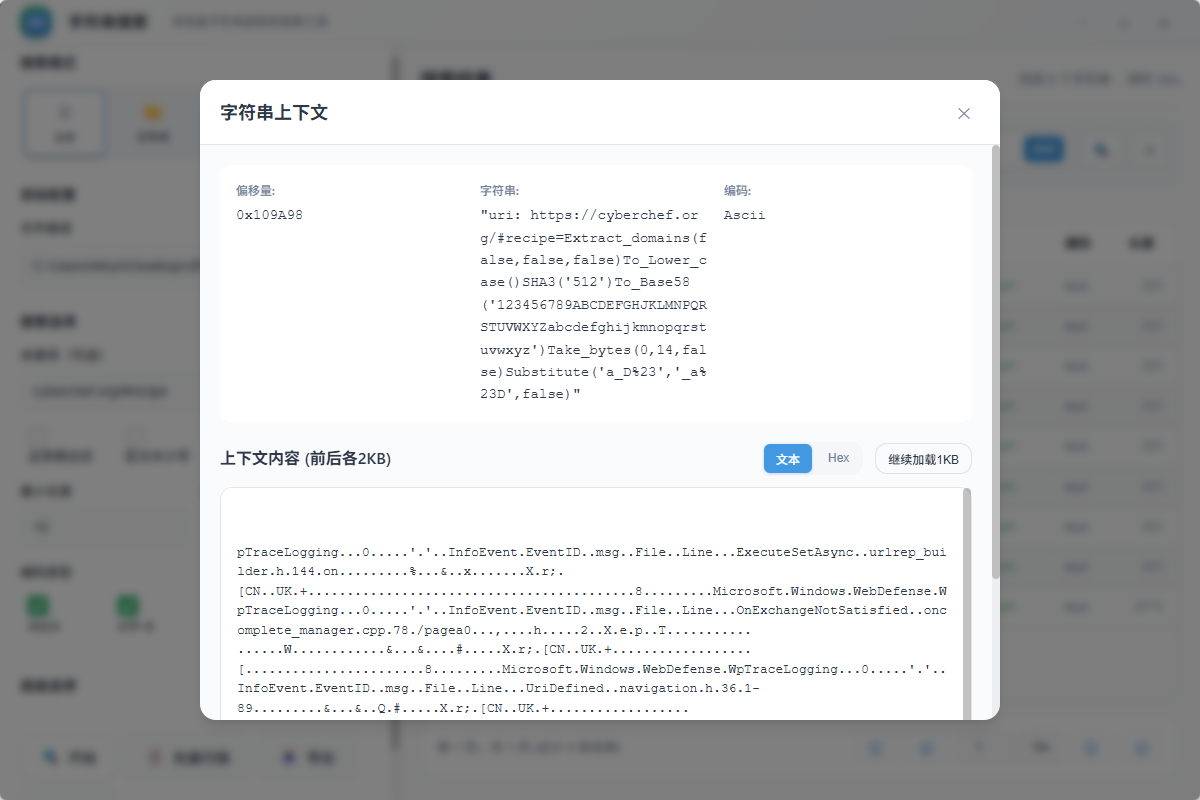
https://cyberchef.org/#recipe=Extract_domains(false,false,false)To_Lower_case()SHA3('512')To_Base58('123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz')Take_bytes(0,14,false)Substitute('a_D%23','_a%23D',false)
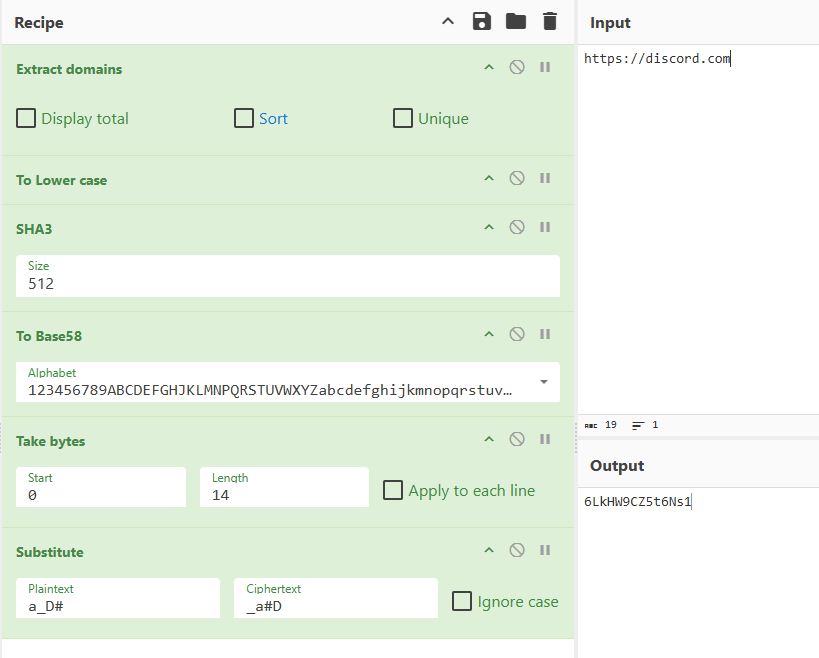
Q7 主密钥
\Root\Users\jack\AppData\Roaming\uTools\database\default\
utools数据库 读取ldb文件即可
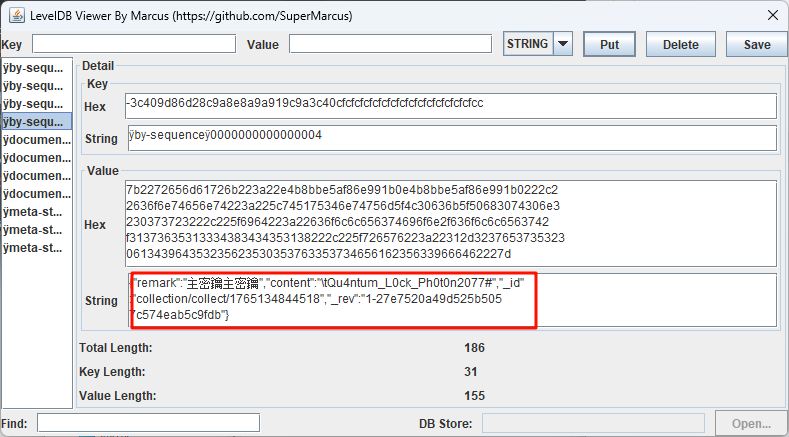
Qu4ntum_L0ck_Ph0t0n2077#
Easy_Base
Zg====AbYQ====wZew====ARZQ====gbaQ====QcdQ====QZdQ====gYaQ====QZcg====QadA====wXcw====QYbg====wZdQ====Qacw====QYZw====AbYQ====AZaQ====wbcg====QZZw====Qacw====Qf为单个字符的Base64正反交替
翻转后得到
Zg==bA==YQ==Zw==ew==RA==ZQ==bg==aQ==cQ==dQ==ZQ==dQ==Yg==aQ==ZQ==cg==aQ==dA==Xw==cw==YQ==bg==Zw==dQ==aQ==cw==YQ==Zw==bA==YQ==ZA==aQ==bw==cg==ZQ==Zw==aQ==cw==fQ==解码得到flag flag{Deniqueubierit_sanguisagladioregis}
Suspicious File
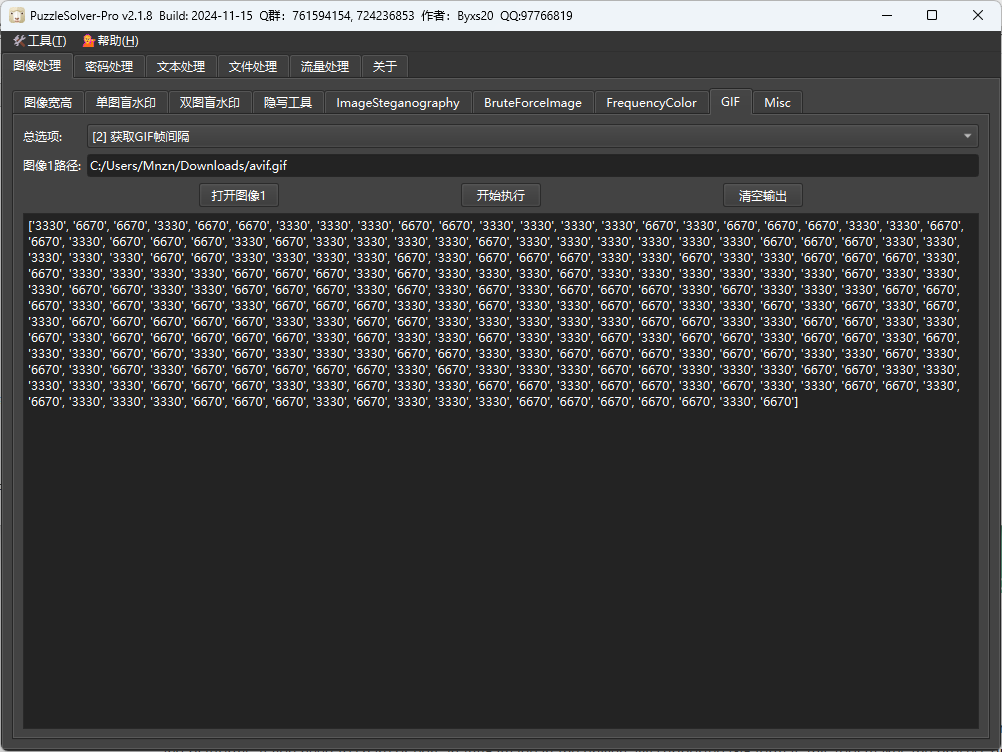
Step1
Base58标准码表解码得到文件
问ai表示是avif文件
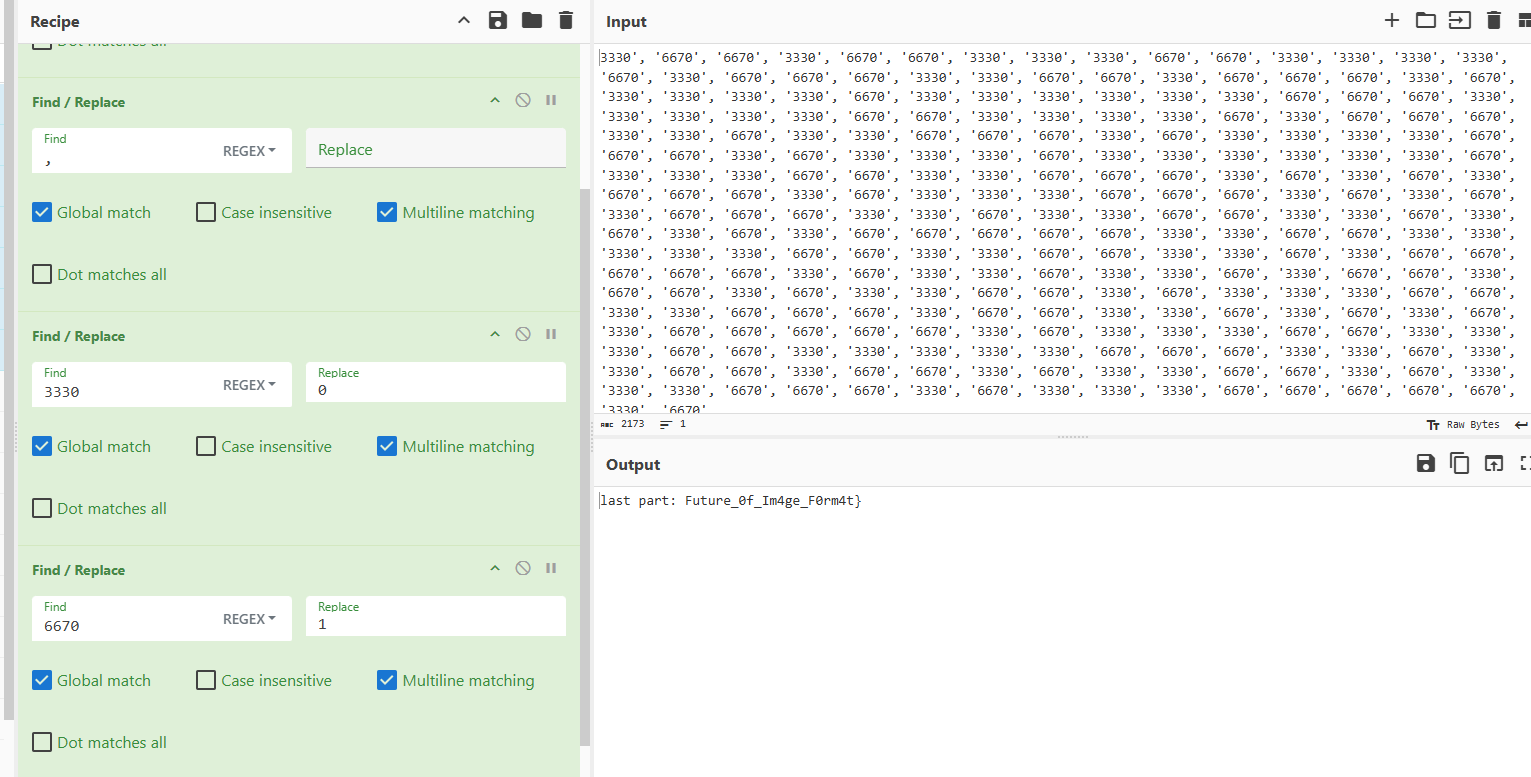
转换成gif
转一下,得到last part: Future_0f_Im4ge_F0rm4t}
Step2
分理出单帧png,LSB,得到 firs t part:hkcert25{AVIF_Will_Be_The_
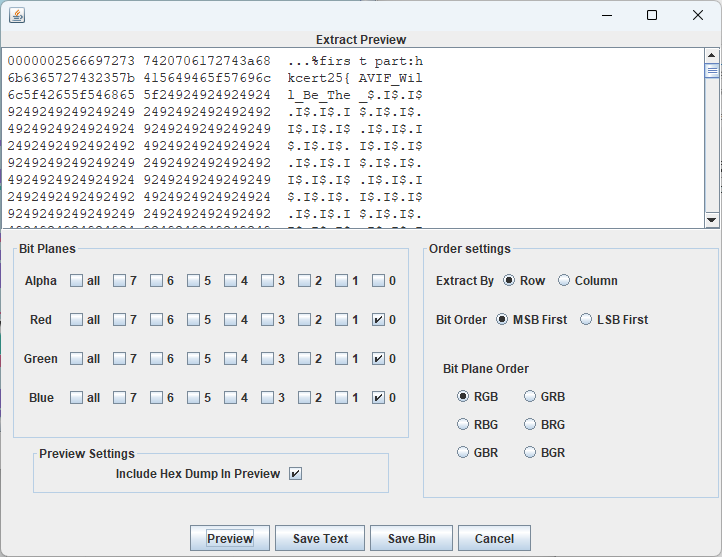
拼接得到完整flag hkcert25{AVIF_Will_Be_The_Future_0f_Im4ge_F0rm4t}
#wp(10)#CTF(9)评论
